Microsoft is not responsible for protecting data in Microsoft 365, so when Oxford Health NHS Foundation Trust—along with the rest of Britain’s National Health Service (NHS)—was transitioning key data and workloads to Microsoft 365, the network management team needed a robust and proven data protection solution.
Read why you need Veritas with Microsoft 365
Data Compliance and Governance

In this post, we will cover:
- Veritas Alta™
- What is different about Veritas compared to other providers?
- Veritas Alta™ Key Features
- Veritas and Microsoft 365
The digital landscape has evolved from being an optional choice to an absolute necessity for the survival of many businesses. However, it's worth reflecting on how many businesses are still primarily operating in the physical world, disconnected from the digital realm. Even for those that primarily exist offline, we must address the fate of the data we collectively generate and the increasing prevalence of cloud-native applications like Microsoft 365. Did you know that Microsoft is not responsible for protecting your data in Microsoft 365?
Therefore, in today's business landscape, regulatory compliance and risk management are taking on ever-greater significance and, potentially, higher costs. As more and more organisations embrace cloud-based services, the burden of managing hybrid cloud environments and striking the right balance between cost and scalability grows, all while ensuring adherence to industry regulations.
Staying ahead of regulatory requirements and implementing strong data governance strategies is crucial for maintaining compliance and safeguarding consumer data. The challenge lies in delivering innovative technology solutions while effectively managing expenses. This necessitates optimising current infrastructure and exploring cost-efficient cloud solutions to achieve more with less.
The Albanese Government introduced increased in penalities for repeated or serious privacy breaches as Australians have the right to expect their data will be protected.
Let's make data governance a top priority, not something we think about later. The changing landscape of threats and work setups has made data governance more complex and crucial than ever. Knowing where your data is located becomes absolutely vital, especially in the aftermath of a ransomware attack.
Organisations should strive to maintain complete control over their enterprise data protection, application resilience, data compliance, and governance. Achieving comprehensive data observability by capturing and archiving data across your entire ecosystem and identifying what truly matters is key
Questions arise about how Microsoft 365 data is stored, safeguarded, and whether businesses are adequately prepared to manage it. The notion of archiving and retrieving digital files should ideally be straightforward, but it's often far from it, unless you have a tool that specialises in that space. The ongoing debate persists, leaving us to wonder how we can effectively allocate business funds towards data management and security. Companies that generate substantial data or depend on data have trusted Veritas for years. An example of this trust is evident in organisations like the Oxford Health NHS Foundation Trust.
Veritas currently protects 91% of the Fortune 100 companies.
Veritas Alta™
Did you know that Veritas offers an innovative suite of cloud solutions designed to help you stay compliant with ever-evolving regulations, while ensuring your data is always secure and available?
Veritas Alta™ is a comprehensive cloud data management solution that assists businesses in elevating their operations through effective data visibility, security, backup, and overall data control across diverse cloud environments. In addition to maintaining high data availability and compliance with regulatory requirements.
Veritas advanced data management tools offer:
- Archive and retention capabilities with the flexibility and scalability to manage data effectively, on-premises or in the cloud.
- Proactive monitoring to investigate potential threats with unparalleled speed, accuracy, and efficiency
- Ability to turn dark data into actionable insights.
- Ability to configure, manage, and control application workflows.
- Support to collect, review, and produce electronically stored information for your organization’s legal and investigation needs.
Download Veritas Alta Data Compliance and Governance to get greater visibility, context, and control with Veritas compliance solutions!
In a study and report published by Vanson Bourne and Veritas surrounding cloud-provided security tools revealed 99 percent of organisations surveyed use security tools to some extent. And 76 percent expressed dissatisfaction with the current offerings from public cloud service providers, believing that they fall short of their organisation's security requirements. Additionally, 89 percent of these organisations reported experiencing ransomware attacks targeting data within their cloud environments.
Veritas Alta™ Ransonware Resiliency
Veritas Alta™ has unmatched ransomware resiliency as it deploys multiple layers of security, including system hardening, AI-based anomaly detection, malware scanning, and immutability, effectively reducing the attack surface and fortifying data protection. Veritas Alta™ also provides flexibility in recovery, offering intelligent and automated orchestration and cost-effective recovery rehearsals.
Why is this important?
The recent ransomware incident at Suncor, as reported by CBC, has prompted discussions among experts in the field. Geoffrey Cann, a former Deloitte partner, emphasised that Suncor's response could have been different if they had possessed a comprehensive systems solution that allowed them to maintain their business operations seamlessly. Unfortunately, in this case, Suncor had to resort to replacing all staff laptops, leading to substantial direct losses amounting to millions of dollars due to the resulting downtime and loss of productivity.
Moreover, the consequences of such incidents go beyond immediate financial impacts. Suncor's reputation suffered a blow, and even loyalty programs were affected. Chester Wisniewski, Chief Technology Officer (CTO) at Sophos, noted the unusual extent to which hardware was compromised, necessitating a full-scale replacement.
Tim McMillan, a Partner at the consulting firm Garrison Strategy, underscored the inevitability of cyberattacks, emphasising that no organisation can completely prevent them. Instead, the focus should be on implementing the right levels and stages of security measures to mitigate the impact of attacks, ensuring that vulnerabilities, when exploited, do not lead to catastrophic consequences for the company.
What is different about Veritas compared to other providers?
Resiliency
- Quickly archive and restore data for Teams, Exchange, SharePoint, OneDrive
- Encrypt data in transit and at rest
- Easily restore user-defined snapshots
Compliance
- Support content from both open-source and proprietary sources
- Quickly adhere to regulatory requests from the SEC, FINRA, FDA, HIPAA, GDPR, FOIA, CPRA
- Archive messages and metadata with an immutable audit trail
Insights
- Leverage in-depth analysis to comply with evolving data regulations.
- Search, classify, and archive hundreds of file types in multiple languages.
- Use OCR on images while categorising audio/video files for better search results.
Veritas Alta™ Key Features
Veritas Alta™ does more than having unmatched ransomware resiliency to safeguard your data. The following distinctive benefits set this cloud solution apart from other cloud service providers.
Optimisation of Application Performance, Availability, and Resiliency
Veritas Alta offers comprehensive application resiliency solutions that cater to all major cloud infrastructures, be it virtual, containerised, or bare metal.
These unified tools play a pivotal role in ensuring the uninterrupted performance of your critical services in several critical ways:
- They facilitate the creation of highly available applications within a multi-cloud environment.
- They empower your organisation with the agility to adapt and scale in response to evolving business requirements.
- They simplify the process of migrating applications between public and private cloud environments or transitioning them back to on-premises infrastructure when necessary.

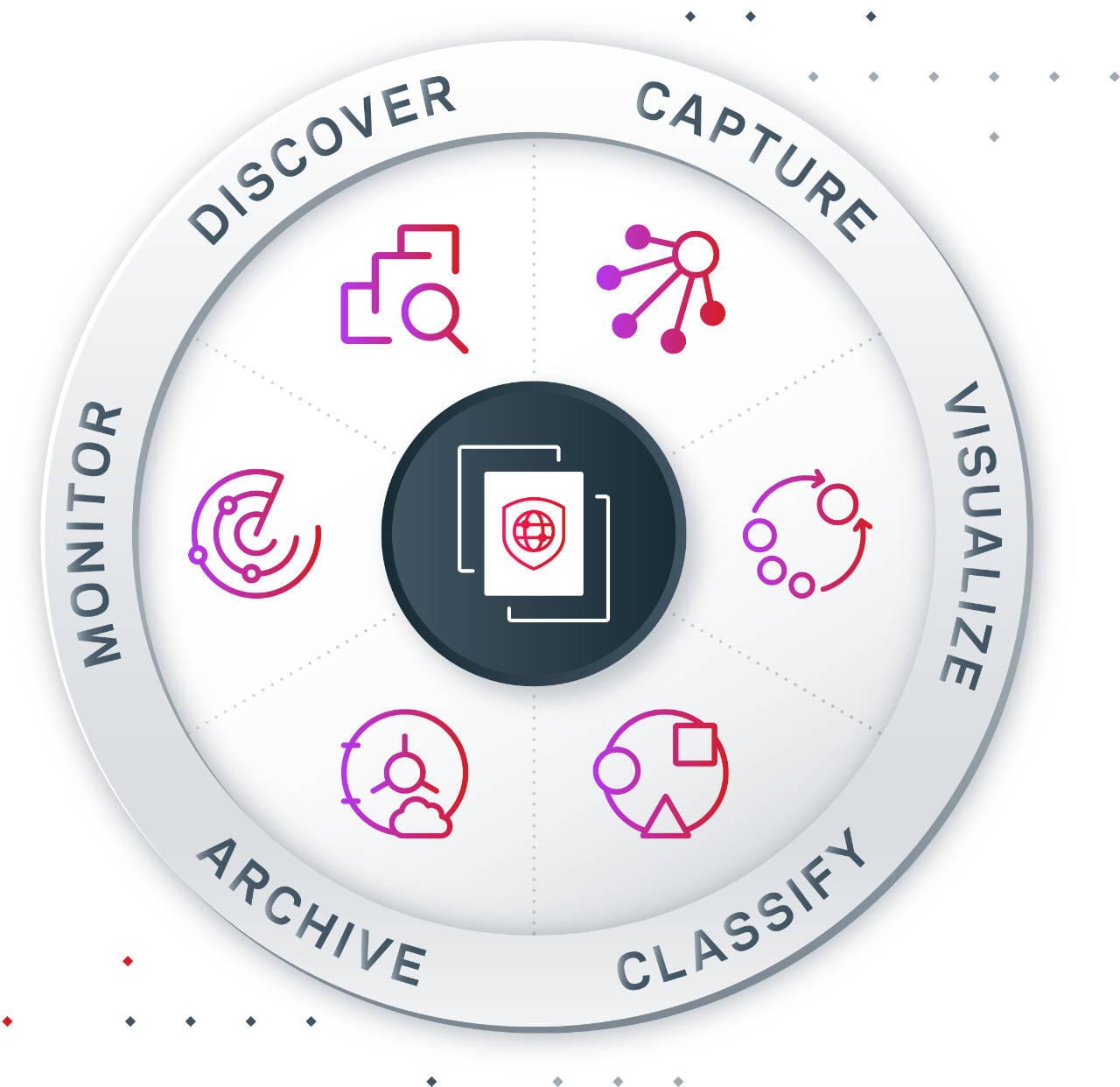
Illuminate and Remediate Information Risk
Veritas stands as the top choice in the industry for data capture and content classification. Their suite of solutions is unrivaled, offering versatile deployment options that span on-premises, IaaS, hybrid, virtual, and SaaS environments.
Their compliance and governance solutions bring together cloud capabilities, empowering organisations to make well-informed decisions regarding their entire data repository. With Veritas Alta, you can automate the classification of content, effortlessly pinpoint pertinent data for legal proceedings, eliminate obscure or "dark data" to mitigate risks, and optimise the overall footprint of your data.
So how does this solution come together with Microsoft 365?
Although Microsoft 365 does offer some data protection features, many customers opt to enhance it with Veritas solutions for several compelling reasons:
Comprehensive Data Protection
While Microsoft 365 provides basic data protection features such as version history and retention policies, Veritas offers a more comprehensive suite of tools for data backup, recovery, and archiving. Veritas ensures a finer level of data protection, adaptable to various needs, guaranteeing no critical information gets overlooked.
Comprehensive Data Coverage
Microsoft 365 is feature-rich, and Veritas ensures you don't miss a single aspect. From Exchange Online to SharePoint, OneDrive for Business, and Teams, Veritas covers it all. Your entire Microsoft 365 ecosystem is safeguarded.
Ransomware Resilience
Ransomware attacks pose a substantial threat, including to data stored within Microsoft 365. Veritas offers ransomware-resilient backups, assuring your organisation of clean data recovery in the event of a ransomware incident. This minimises downtime and data loss.
Enhanced Security
While Microsoft 365 secures data in transit and at rest, Veritas adds an extra layer of security. This includes features like immutable audit trails, safeguarding data against tampering or deletion, therefore upholding data integrity.
Customised Solutions
Every business has unique data protection needs. Veritas empowers customers to tailor their data protection strategies to align with their specific requirements. This flexibility proves invaluable for businesses with intricate data protection needs.
Regulatory Compliance
Diverse industries and regions enforce specific data retention and compliance regulations. Veritas solutions simplify compliance for organizations, offering comprehensive archiving and audit trail features, ensuring regulatory obligations are met.
Data Insights
Veritas provides advanced data analysis capabilities, enabling organisations to gain insights, classify data, and manage it more effectively. These insights play a pivotal role in meeting data compliance requirements and optimizing data management practices.
Seamless Migration
For organisations eyeing cloud environment transitions or shifts from on-premises systems to the cloud, Veritas streamlines and automates migration processes, guaranteeing secure and efficient data transfers.
Cost Optimisation
Veritas actively archives less frequently used data, assisting businesses in optimising storage costs, especially in cloud-based solutions like SharePoint Online. This translates to long-term cost savings.
Data Recovery Options
Veritas offers more flexible data recovery options, facilitating easy restoration of items, folders, mailboxes, or entire sites. This flexibility proves indispensable in addressing various data loss scenarios.
Scalability
Veritas solutions are scalable, capable of accommodating the growing data volumes of organizations, making them a suitable long-term choice.
While Microsoft 365 provides a fundamental level of data protection, Veritas solutions offer a more robust, adaptable, and feature-rich approach to data protection and management. Organisations prioritising data security, compliance, flexibility, and advanced features frequently choose to complement Microsoft 365 with Veritas to ensure comprehensive data management, protection and security for peace of mind.
Konverge is a Veritas Partner
We're here to help you with your questions and if you want to learn about the latest Veritas offers and promotions.
Simply fill in your details below and one of our techies will reach out to you.
Contact Me About Veritas