Executive's Guide To Data Loss Prevention
The Practical Executive's Guide to Data Loss Prevention (DLP)
"It’s not the technology behind DLP controls that ultimately determines your success— it’s the methodology and execution strategy of your vendor that governs both your experience and results.”
Forcepoint
The Problem of Data Loss in Australia
Australian businesses, like those in other parts of the world, face a variety of specific challenges in the realm of data security. These challenges are shaped by the unique economic, regulatory, and technological landscape of Australia. Here are some of the key challenges:
Adapting to Rapidly Changing Technology and Threat Landscapes
The technology landscape is evolving rapidly, and with it, the threat landscape changes too. Businesses need to be agile in adapting their cybersecurity strategies to these changes.
Awareness and Training
A recurring challenge is the lack of cybersecurity awareness among employees. Human error remains a leading cause of data breaches, and ongoing education and training are essential to mitigate this risk.
Compliance with Regulatory Frameworks
Australian businesses must comply with a range of local and international data protection regulations. The most notable is the Australian Privacy Act and the Australian Notifiable Data Breaches (NDB) scheme. Compliance requires a deep understanding of these regulations and the implementation of data protection measures.
Compliance with Consumer Expectations
Australian consumers are increasingly aware of and concerned about data privacy. Businesses must not only protect data for compliance reasons but also to maintain consumer trust and satisfaction.
Cybersecurity Threats
Similar to businesses in other parts of the world, Australian businesses encounter a range of cyber threats such as ransomware, phishing attacks, and advanced persistent threats (APTs). The complexity and frequency of these attacks continue to escalate.
Data Sovereignty and Cross-Border Data Flow
For businesses operating in multiple jurisdictions, including international markets, there's a challenge in managing data sovereignty. Ensuring that data stored or processed outside of Australia complies with local laws can be complex.
Emerging Technologies and Data Proliferation
The rapid adoption of emerging technologies like the Internet of Things (IoT), cloud computing, and big data analytics has led to massive data proliferation. Managing and securing this data, while leveraging it for business advantage, is a significant challenge.
Supply Chain and Third-Party Risks
Australian businesses often rely on third-party vendors and global supply chains, which can introduce vulnerabilities if these partners are not adequately secured. Managing these risks requires thorough due diligence and continuous monitoring.
Resource Constraints
Small and medium-sized enterprises (SMEs) often face resource constraints, lacking the budget and expertise to implement effective cybersecurity measures.
Remote and Hybrid Work Environments
The shift towards remote and hybrid work models, accelerated by the COVID-19 pandemic, has introduced new security challenges. Businesses must secure data across distributed networks and a variety of devices, many of which may not be under the direct control of IT departments.
From Vision to Implementation
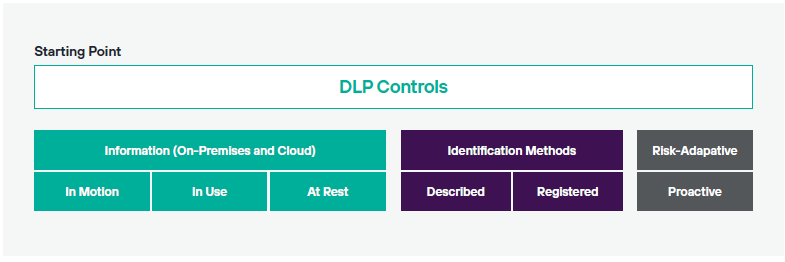
While various Data Loss Prevention (DLP) controls offer similar functionalities, it is important to recognise that not all technology providers share the same perspective on how DLP can effectively address data loss issues. Therefore, your initial step should involve understanding the methodology and execution strategy of each provider.
When you enquire about a tech provider's methodology, you are essentially seeking insight into their vision for how their tool addresses the challenge of data loss. This will reveal the vendor's unique capabilities and the trajectory of its roadmap. For decision-makers, understanding the "why" behind actions is consistent to success and long-term satisfaction than merely understanding the "what."
A vendor's methodology significantly shapes its execution or implementation strategy. For example, if one vendor focuses on assessing data-at-rest while another prioritises evaluating data-in-motion using risk-adaptive controls, their execution strategies diverge significantly. The manner in which a vendor implements DLP controls is crucial, impacting both the total cost of ownership (TCO) and the expected time-to-value. These factors are pivotal in making informed purchasing decisions and aligning expectations with stakeholders.
It is imperative to note that applying one vendor's methodology to another's technology is ill-advised. The methodology defines and propels a vendor's technology roadmap, and merging the two aspects risks investing in a technology that falls short of meeting long-term needs.
Quantifiable and Pragmatic Approaches
If you've attended conferences or delved into DLP best practices, you might be familiar with the metaphorical advice, "don't try to boil the ocean." Essentially, this cautionary statement implies that executing a complete DLP program in one go is impractical. However, this guidance lacks practicality as it fails to provide a roadmap for action. In some instances, "don't boil the ocean" appears more as a warning rather than a constructive best practice. (Forcepoint Whitepaper)
Arguably, many published best practices often prove impractical due to resource constraints or organisational challenges. Striking the right balance between data security and accessibility is crucial. Overly stringent, fixed policies can hinder productivity and pose risks to businesses.
The real value lies in practical best practices that consider the cost, benefits, and effort required for implementation, which can be measured to assess their feasibility for adoption.
To ensure your DLP control is both measurable and practical in managing and mitigating the risk of data loss, it's essential to grasp two key pieces of information:
- Measurability necessitates understanding and applying the risk formula for data loss. While similar to other risk models, the risk formula for data loss possesses a significant difference, as elaborated below.
- Practicality requires understanding where a high-impact data breach is most likely to occur and leveraging the 80/20 rule to focus attention and resources on the most critical areas.
Konverge stands out in the crowded landscape of systems integrators and technology providers, with its distinctive vision for partnering with Forcepoint to provide exceptional Data Loss Prevention (DLP) solutions. By partnering with Konverge, you align yourself with Forcepoint that doesn't just offer generic DLP solutions but tailors them to fit seamlessly into your unique business ecosystem.
Download Forcepoint's Whitepaper for more information.
Fill In The Below To Download Whitepaper
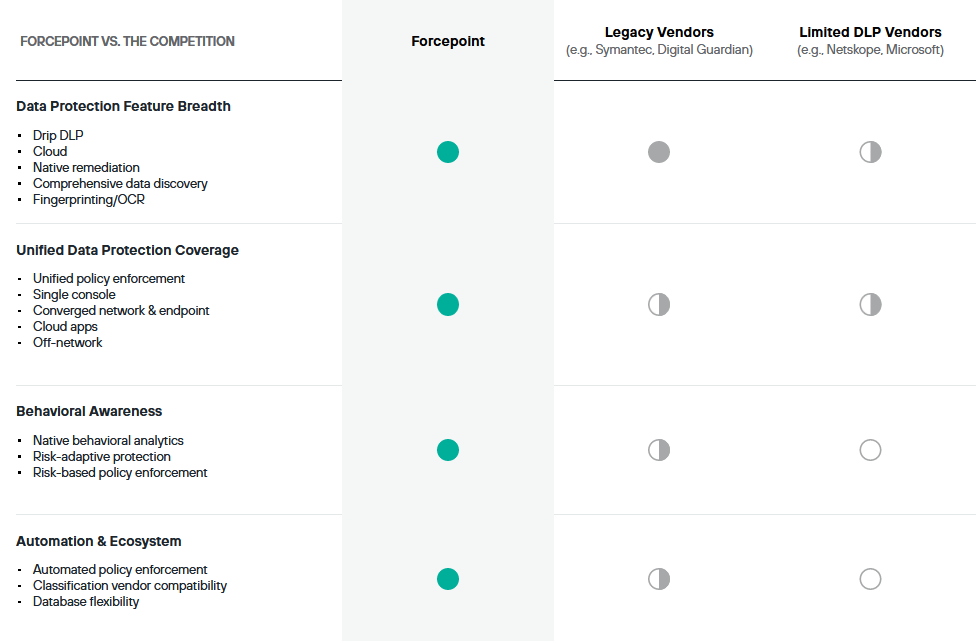
Why Forcepoint DLP?
Fill In Below to Download DLP Comparison











