Comparing Next-Generation Firewall Solutions Palo Alto Network vs Cisco Secure Firewall
Comparing Palo Alto Networks Next-Gen Firewall vs. Cisco Secure Firewall (Firepower)

Understanding Next-Generation Firewalls
NGFWs provide advanced security measures like intrusion prevention, application control, and cloud-based threat intelligence. These tools combat increasingly sophisticated cyber threats while supporting enterprise scalability and performance needs.
Palo Alto Networks NGFW: Leading with Innovation
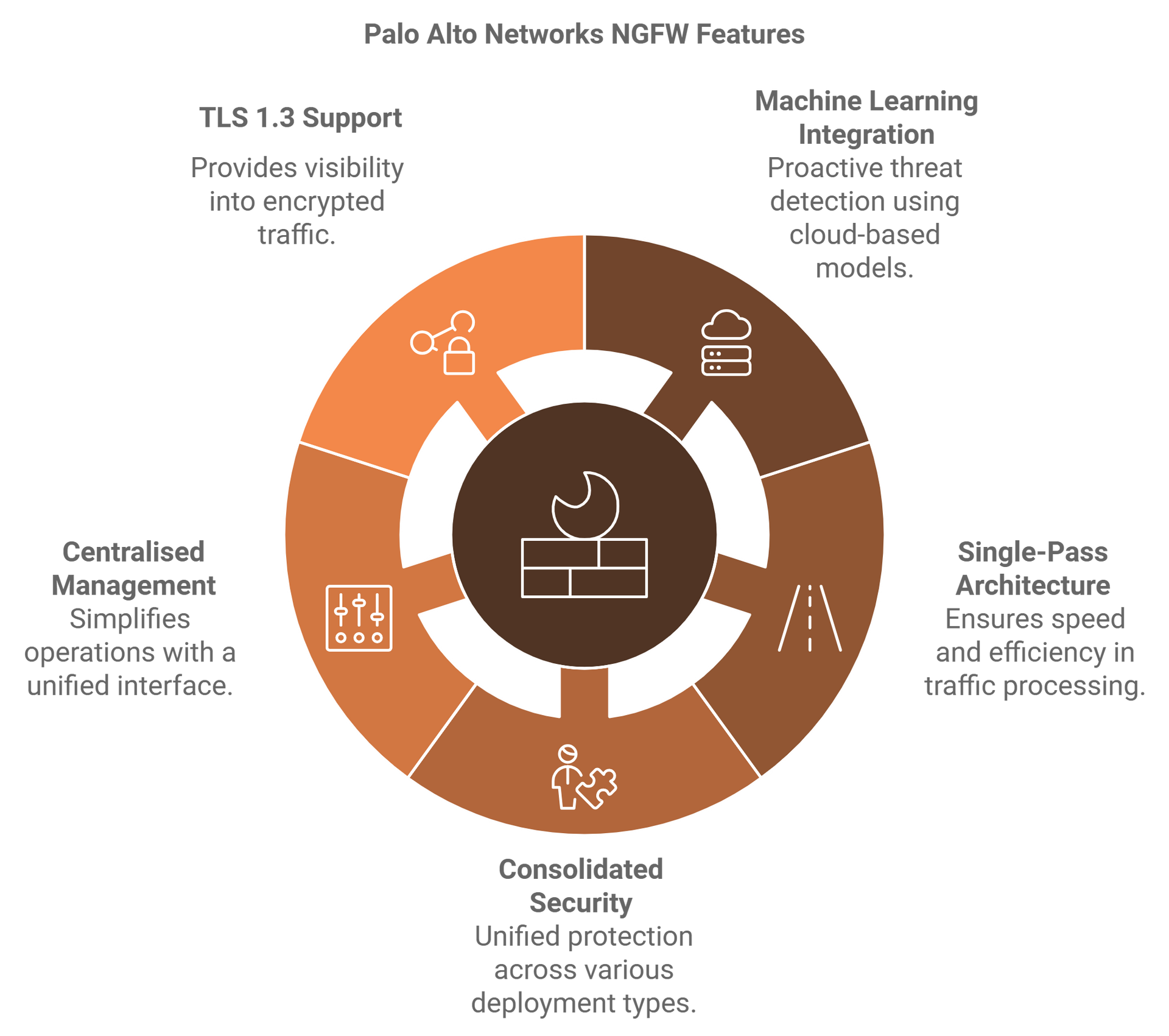
Key Strengths
Machine Learning for Threat Detection:
Palo Alto Networks is the first NGFW provider to integrate inline machine learning for proactive threat prevention. Its systems leverage cloud-based ML models like WildFire and DNS Security, providing real-time updates without performance degradation.
Single-Pass Architecture:
Offers predictable performance by processing all traffic analysis and policy enforcement in a single stream. This ensures no compromise on speed, even when multiple security features are active.
Consolidated Security Across Platforms:
Palo Alto's NGFW supports hardware, virtual machines, containers, and as-a-service models, delivering consistent and centralised security across diverse deployment types.
Centralised Management:
The Panorama management interface simplifies operations by allowing all features to be configured on a single platform, unlike Cisco's multiple disconnected interfaces.
TLS 1.3 Support:
With hardware-accelerated decryption capabilities, Palo Alto fully supports TLS 1.3, providing comprehensive visibility into encrypted traffic.
Challenges:
Palo Alto Networks’ solutions are premium-priced, which may pose budgetary challenges for smaller organisations.
Cisco Secure Firewall (Firepower): Familiarity with Limitations
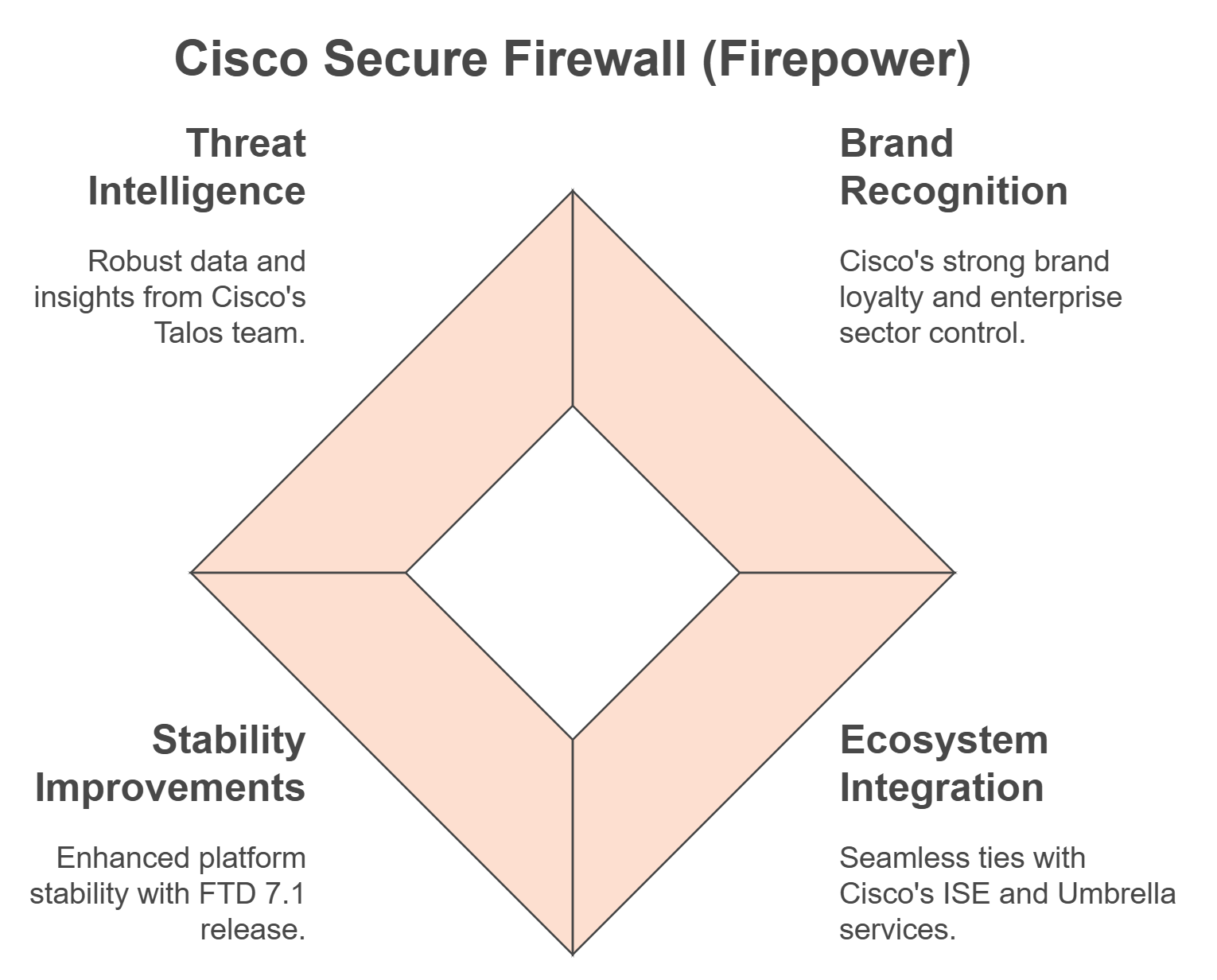
Key Strengths
Brand Recognition:
Cisco enjoys strong brand loyalty and extensive account control in the enterprise sector.
Integration with Cisco Ecosystem:
Native ties with Cisco Identity Services Engine (ISE) and Umbrella make it appealing to organisations deeply entrenched in Cisco's ecosystem.
Improved Stability:
The Firepower Threat Defense (FTD) 7.1 release has seen significant bug fixes, stabilising the platform compared to earlier versions.
Threat Intelligence through Talos:
Cisco's Talos research team provides robust data collection and threat insights.
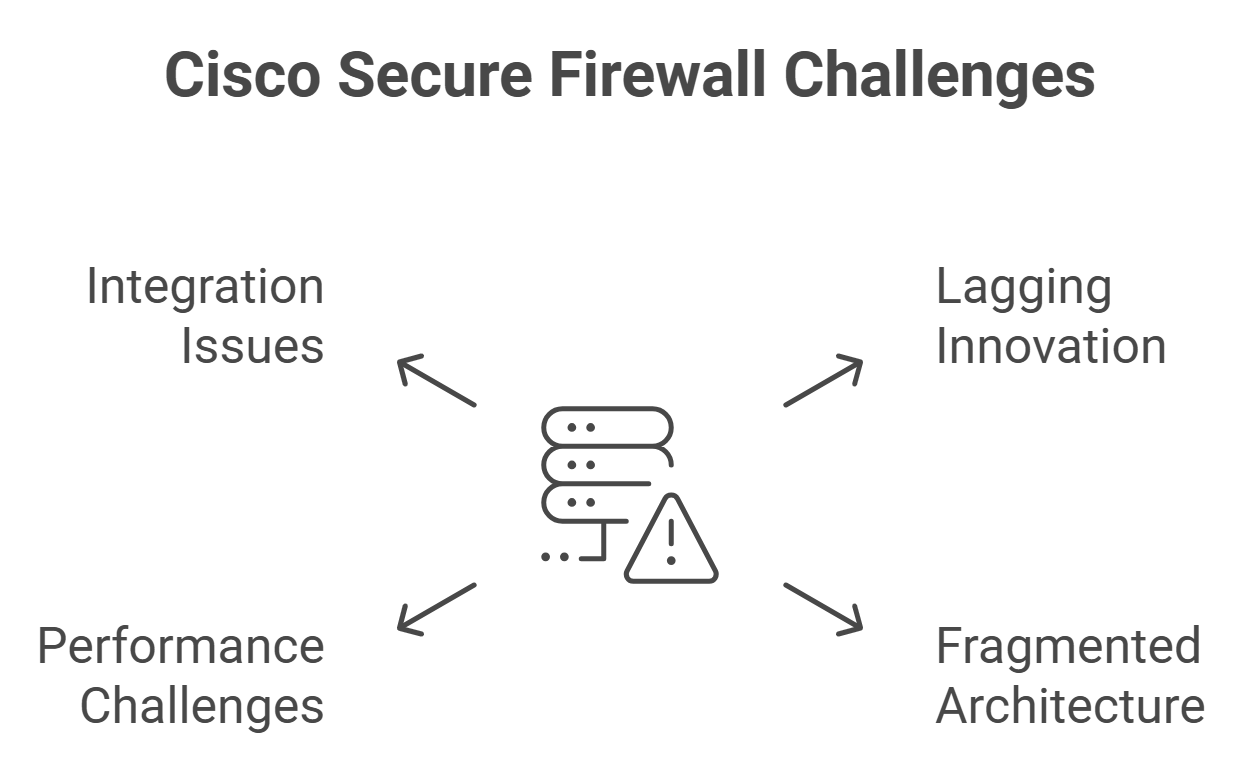
Weaknesses
Lagging Innovation:
While competitors like Palo Alto offer groundbreaking advancements, Cisco's Firepower continues to rely on legacy architecture and lacks innovation in critical areas like inline machine learning.
Fragmented Architecture:
Cisco's approach requires multiple separate tools (e.g., FMC, FDM, CDO), making integration and management cumbersome. The Firepower solution is effectively a combination of acquisitions rather than a natively engineered platform.
Performance Challenges:
SSL decryption and sandboxing significantly degrade performance. Additionally, Cisco's metrics often exclude critical features in their datasheets, presenting an inflated performance image.
Integration Issues:
Despite marketing claims, Cisco struggles with seamless integration across its product portfolio, often requiring expensive professional services.
Feature Comparison Matrix
| Feature | Palo Alto Networks NGFW w/ PAN-OS 10.1 | Cisco FTD 7.1 |
|---|---|---|
| Inline Machine Learning | Yes | No |
| Predictable Performance with All Threat Prevention Sigs Due to Single-Pass Architecture | Yes | No (ASA code branches off to Snort process for IPS/L7 inspection) |
| TLS 1.3 Full Support | Yes | Partial (Certificate-Only Decryption) |
| Centralised Management | Yes, Panorama— while also allowing direct management | No, mix of FMC, FDM, CSM, CDO, and ASDM in hybrid environments |
| Threat Intelligence Integration | Comprehensive | Limited |
| OS Support for Malware Analysis | Windows, Linux, macOS, Android | Windows only |
| SD-WAN Capabilities | Built in | Viptela (full feature) Meraki (branch connectivity) |
| DLP and Inline SaaS | Yes | No, both require separate appliance/ service |
| Embedded L4-to-L7 Policy Migration | Yes (Policy Optimiser) | No |
| MFA Gateway | Yes | No |
| Automatic Submission of All Supported File Types for Malware Analysis | Yes | No |
| Consistent Feature Parity Across Firewall Product Line | Yes | No, features depend on architecture (ASA, ASA + Firepower, FTD, Meraki) |
Palo Alto Networks: Delivering ROI with Comprehensive Security
Palo Alto’s unified approach offers a higher return on investment through ease of use, reduced risk, and the ability to scale seamlessly. Its solutions prioritise long-term efficacy with features like:
- Bare-metal malware analysis.
- Inline SaaS security.
- Advanced SD-WAN capabilities.
In contrast, Cisco’s reliance on legacy systems and fragmented solutions can create operational inefficiencies, driving up costs in the long run.
Making the Right Choice for Your Enterprise
When comparing Palo Alto Networks NGFW to Cisco Secure Firewall (Firepower), the decision comes down to priorities:
- Performance and Innovation: Palo Alto leads with advanced technology and streamlined management.
- Brand Familiarity: Cisco appeals to enterprises already invested in its ecosystem, albeit with significant operational trade-offs.
By investing in solutions like Palo Alto Networks, organisations can future-proof their cybersecurity strategies while ensuring robust, consistent, and efficient protection.
Source: Palo Alto Networks NGFW vs. Cisco Secure Firewall (Firepower)











