What Is Precision AI by Palo Alto Networks
What Is Precision AI™?
Picture this: Keanu Reeves, the ultimate guardian of truth and justice, now standing as the face of Precision AI™ by Palo Alto Networks. Imagine his calm yet commanding voice saying, "In a world where AI powers both heroes and villains, only the most precise intelligence can defend your digital universe."
Just like Neo in The Matrix, Precision AI™ is built to anticipate and neutralise attacks before they happen. It’s the cybersecurity solution that rewrites the rules, fusing advanced AI with real-world expertise to stop threats in real time.
Keanu asks: "Are you ready to choose the red pill and unlock the future of cyber defense?"
Precision AI™ – Because the only way to fight AI-driven threats is with precision.
Precision AI™ is Palo Alto Networks' proprietary AI system that combines machine learning, deep learning, and generative AI to enhance cybersecurity capabilities. It aims to provide real-time security and safety across Palo Alto Networks' platforms - Strata, Prisma, and Cortex.
Why Precision AI™ Matters
AI is a powerful tool for businesses but also for cybercriminals. Attackers use AI to improve phishing, create new malware, and scale attacks faster than ever. This expands the risks for organisations, making traditional security tools insufficient. Precision AI is designed to counter these threats by using AI to fight AI, offering real-time security that evolves as threats change.
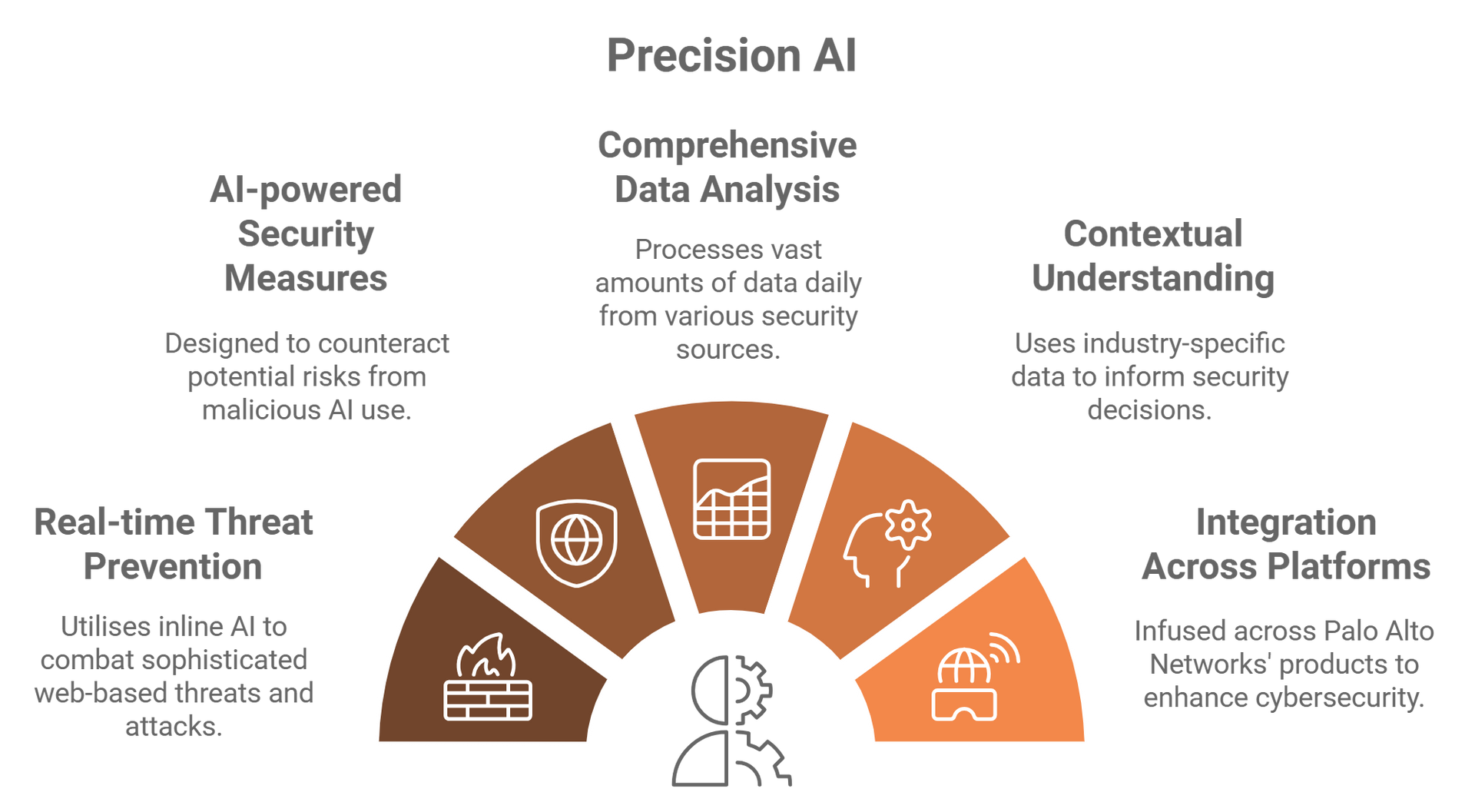
Core Features of Precision AI™
AI infrastructure represents a new and potentially crippling vulnerability. Attacks such as data poisoning or using AI to write malicious code are new vectors that are difficult to identify using traditional security tools and techniques. Products powered by Precision AI™ enable cybersecurity teams to protect AI infrastructure from compromise, using AI models to secure the entire AI roadmap. (Source: Palo Alto site)
Massive Data Utilisation
- Uses one of the largest security data pools in the industry.
- Tracks attack patterns, threat actors, and industry-specific risks to predict and stop attacks.
Custom AI Models
- Combines different AI techniques to accurately detect threats while minimizing false alarms.
- Learns from expert cybersecurity research and real-world data.
Real-Time Threat Detection
- Identifies and blocks new and unknown attacks like zero-day exploits and AI-generated malware.
Benefits of Precision AI
Stops AI-Driven Attacks
- Detects advanced threats like AI-created phishing and malware in real time.
Simplifies Security Operations
- Reduces the workload for security teams by automating tedious tasks.
- Makes tools easier to use with natural language capabilities.
Protects AI Systems
- Secures AI infrastructure from attacks like data poisoning or malicious code creation.
Why Is Precision AI™ Important?
Cybercriminals are leveraging AI to improve attacks, and organisations need AI-powered tools to fight back effectively.
How Precision AI™ Helps
Precision AI™ simplifies security while increasing its accuracy, helping teams respond faster to evolving threats.
Precision AI™ - The Future of Security
Precision AI™ represents a new standard in cybersecurity, giving organisations the tools to protect their systems and use AI safely.
Precision AI™ isn’t just a tool; it’s a necessity in the era of AI-powered threats. It empowers cybersecurity teams to keep pace with attackers and ensures businesses can use AI securely and confidently.
North Dakota
North Dakota IT safeguards citizens with integrated, AI-driven security operations.



Latest Insights

Ask us anything
No matter what your question relates to, our IT specialists will be happy to help with any related enquiries.
We want to hear from you
Send us your details and we’ll get back to you to schedule a time to talk.
Contact us form Konverge footer
We will get back to you as soon as possible
Please try again later








