What is Prisma by Palo Alto Networks
What is Prisma® by Palo Alto Networks

Palo Alto Networks’ Prisma® suite is designed to address the security challenges of modern, distributed environments. It provides solutions for securing cloud applications, remote workforces, branch offices, and hybrid infrastructures, all while incorporating advanced threat prevention, Zero Trust principles, and AI-driven analytics.
Below is a breakdown of key Prisma® products and their roles within cybersecurity:
| Product | Role | Key Features |
|---|---|---|
| Prisma® Access | Secure Access Service Edge (SASE) | Secure remote access, Zero Trust, cloud-delivered firewall, AI-powered security |
| Prisma® Cloud | Cloud-Native Application Protection Platform (CNAPP) | Secures containers, Kubernetes, serverless, continuous compliance, IAM |
| Prisma® SD-WAN | SD-WAN for optimised branch and cloud connectivity | Centralised management, WAN optimisation, secure connections |
| Prisma® SaaS | Next-Generation Cloud Access Security Broker (CASB) | SaaS visibility, DLP, shadow IT monitoring, API and inline security |
Prisma® Access
Palo Alto Prisma Access is a Secure Access Service Edge (SASE) solution that combines network and security functionalities in a cloud-delivered service. It ensures secure access to applications and data for remote workers, branch offices, and mobile users, regardless of location. We will explore the key features of Prisma Access, the industries and markets it serves, the problems it addresses, and its value propositions within the Australian Cybersecurity framework.
Key Features of Palo Alto Prisma® Access
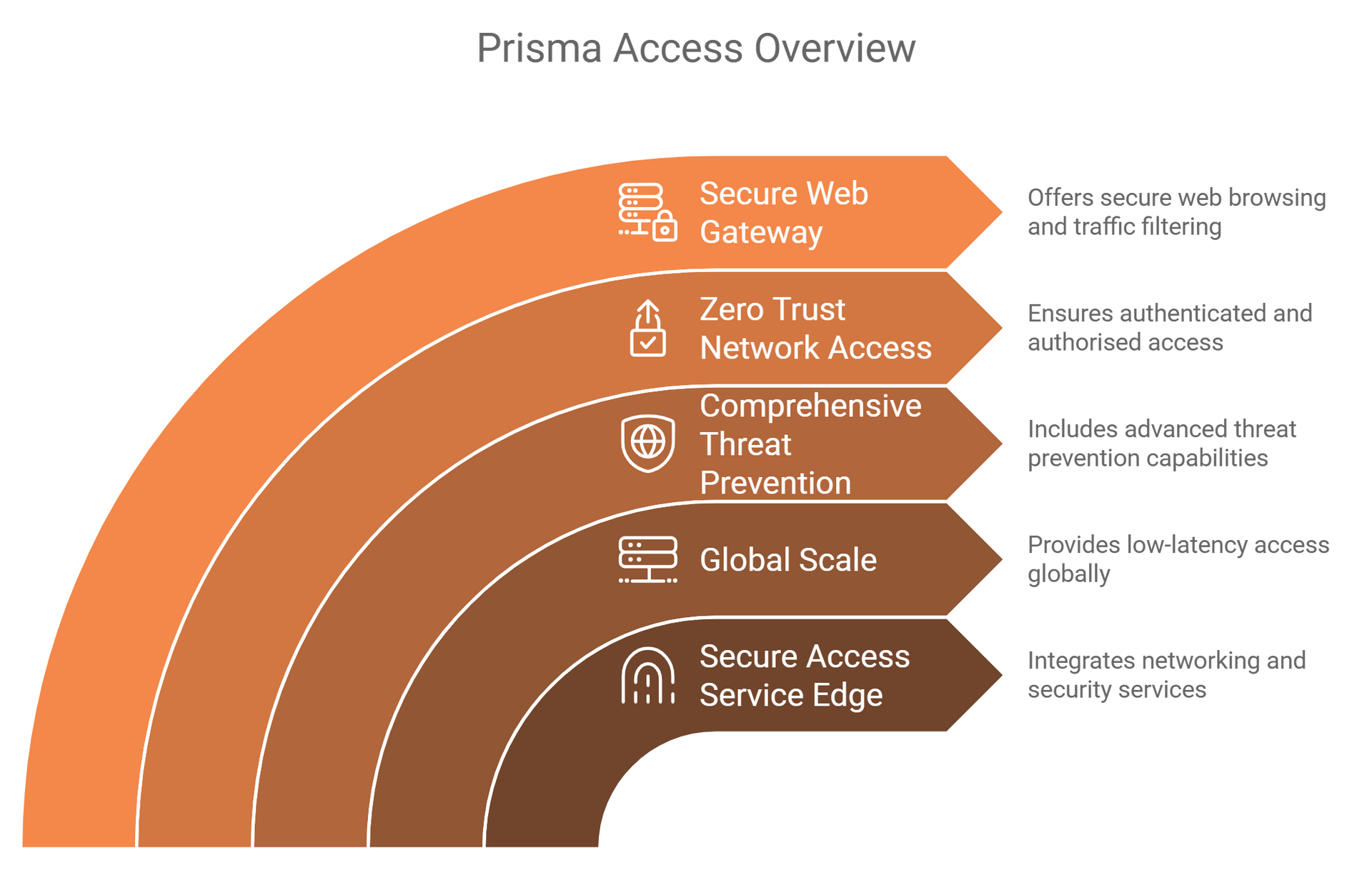
- Secure Access Service Edge (SASE): Prisma® Acess integrates networking and security services into a single cloud-delivered platform, enabling secure access to applications and data from anywhere.
- Global Scale: With a vast network of data centers around the world, Prisma® Access provides low-latency access and high availability for users, ensuring a seamless experience.
- Comprehensive Threat Prevention: Comprehensive data protection, including advanced threat prevention capabilities, such as intrusion prevention, malware analysis, and URL filtering, to protect against a wide range of cyber threats.
- Zero Trust Network Access (ZTNA): Prisma® Access employs a Zero Trust model, ensuring that users are authenticated and authorised before accessing applications, thereby minimising the risk of unauthorised access.
- Secure Web Gateway (SWG): It offers secure web browsing by inspecting and filtering web traffic to prevent data loss and protect against malicious content.
- Cloud Access Security Broker (CASB): Prisma® Access provides visibility and control over cloud applications, helping organizations manage risks associated with shadow IT.
- User Experience Optimisation: The platform includes AI-powered security features that optimise user experience, such as application performance monitoring and traffic shaping.
Industries and Markets Served
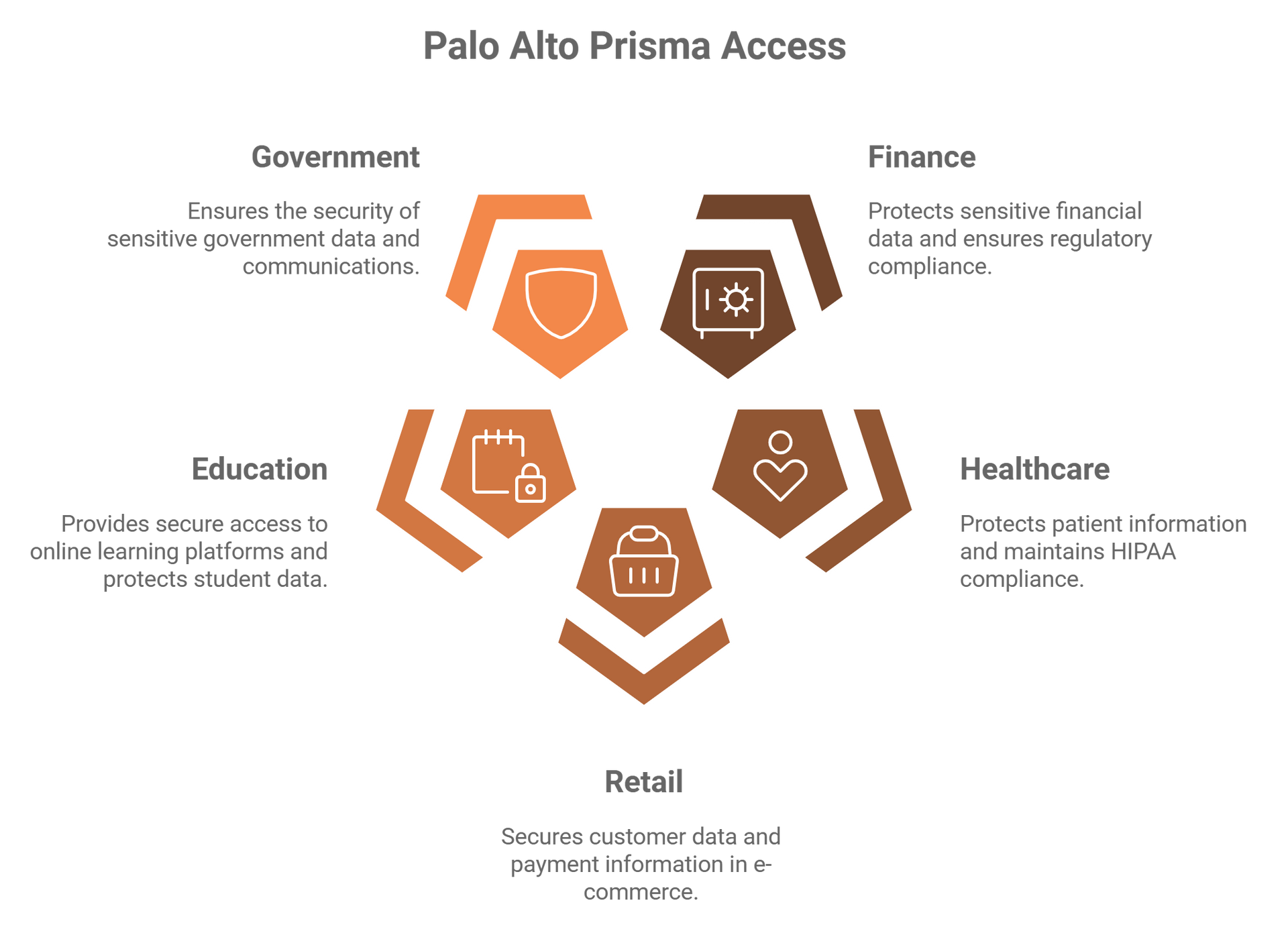
Palo Alto Prisma® Access is applicable across various industries, including but not limited to:
- Finance: Protecting sensitive financial data and ensuring compliance with regulations.
- Healthcare: Protecting patient information and maintaining HIPAA compliance.
- Retail: Securing customer data and payment information in e-commerce environments.
- Education: Providing secure access to online learning platforms and protecting student data.
- Government: Ensuring the security of sensitive government data and communications.
Problems Resolved by Prisma® Access
Prisma Access addresses several key challenges faced by organisations today:
- Remote Work Security: With the rise of remote work, organisations need to secure access to applications and data from various locations.
- Data Breaches: The solution helps prevent data breaches by providing comprehensive threat protection and secure access controls.
- Compliance Requirements: Prisma Access assists organisations in meeting regulatory compliance requirements by providing visibility and control over data access and usage.
- Complex Security Architectures: By integrating multiple security functions into a single platform, Prisma Access simplifies security management and reduces complexity.
Why Invest in Prisma® Access and how it fits within the Australian Cybersecurity Framework?
Palo Alto Prisma® Access aligns with the Australian Cybersecurity framework by offering several value propositions:
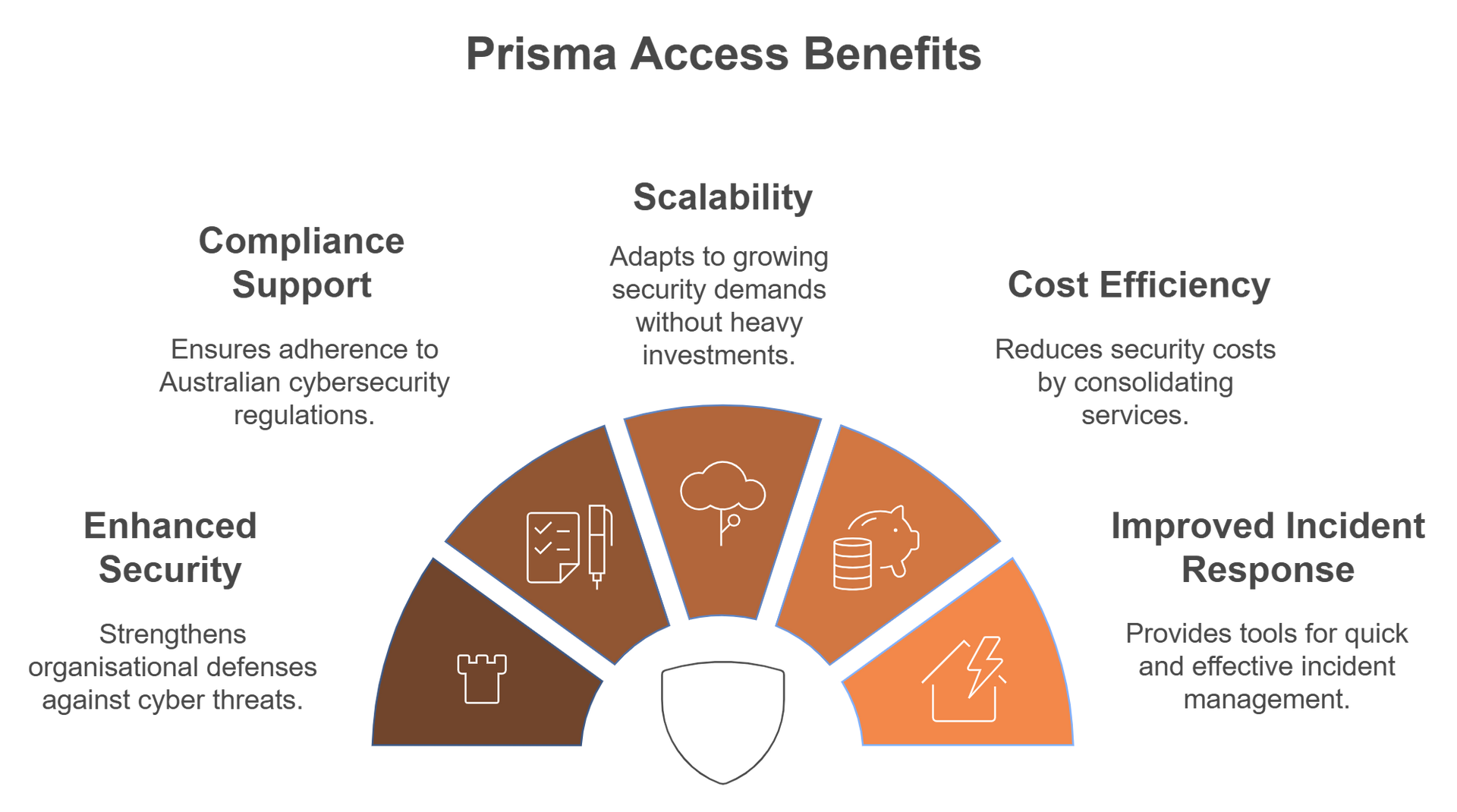
- Enhanced Security Posture: By implementing a Zero Trust approach, organisations can significantly enhance their security posture and reduce the risk of cyber threats.
- Compliance Support: Prisma® Access helps organisations comply with Australian cybersecurity regulations and standards, such as the Essential Eight and the Australian Privacy Principles.
- Scalability: As organisations grow, Prisma® Access can easily scale to meet increasing security demands without the need for significant infrastructure investments.
- Cost Efficiency: By consolidating multiple security services into a single platform, Prisma Access can reduce overall security costs and simplify management.
- Improved Incident Response: The solution provides real-time visibility and analytics, enabling organisations to respond quickly to security incidents and minimise potential damage.
Prisma® Cloud
Prisma® Cloud is a single-vendor, cloud-native application protection platform (CNAPP) designed to protect applications across any public, private, hybrid, or multicloud environment. Unlike point tools, Prisma Cloud integrates a broad set of security capabilities into a single platform to deliver unified, best-in-class security. The benefits of our approach include reduced risk, fewer breaches, better DevSec
collaboration, increased efficiency, and improved compliance and security posture. (Source: Palo Alto Prisma Cloud at a glance).
With Prisma® Cloud, organisations can secure the entire cloud application lifecycle, from development to runtime, enabling a proactive approach to mitigating risks and ensuring compliance in dynamic cloud environments.
In summary, its key features include:
- Security for containers, Kubernetes, serverless functions, and virtual machines.
- Continuous compliance monitoring for regulatory frameworks like GDPR, APRA CPS 234, and ISO 27001.
- Automated misconfiguration detection and runtime protection.
- Identity and access management for cloud assets.
Prisma Cloud Use Case - Risk Prevention
Risk Prevention
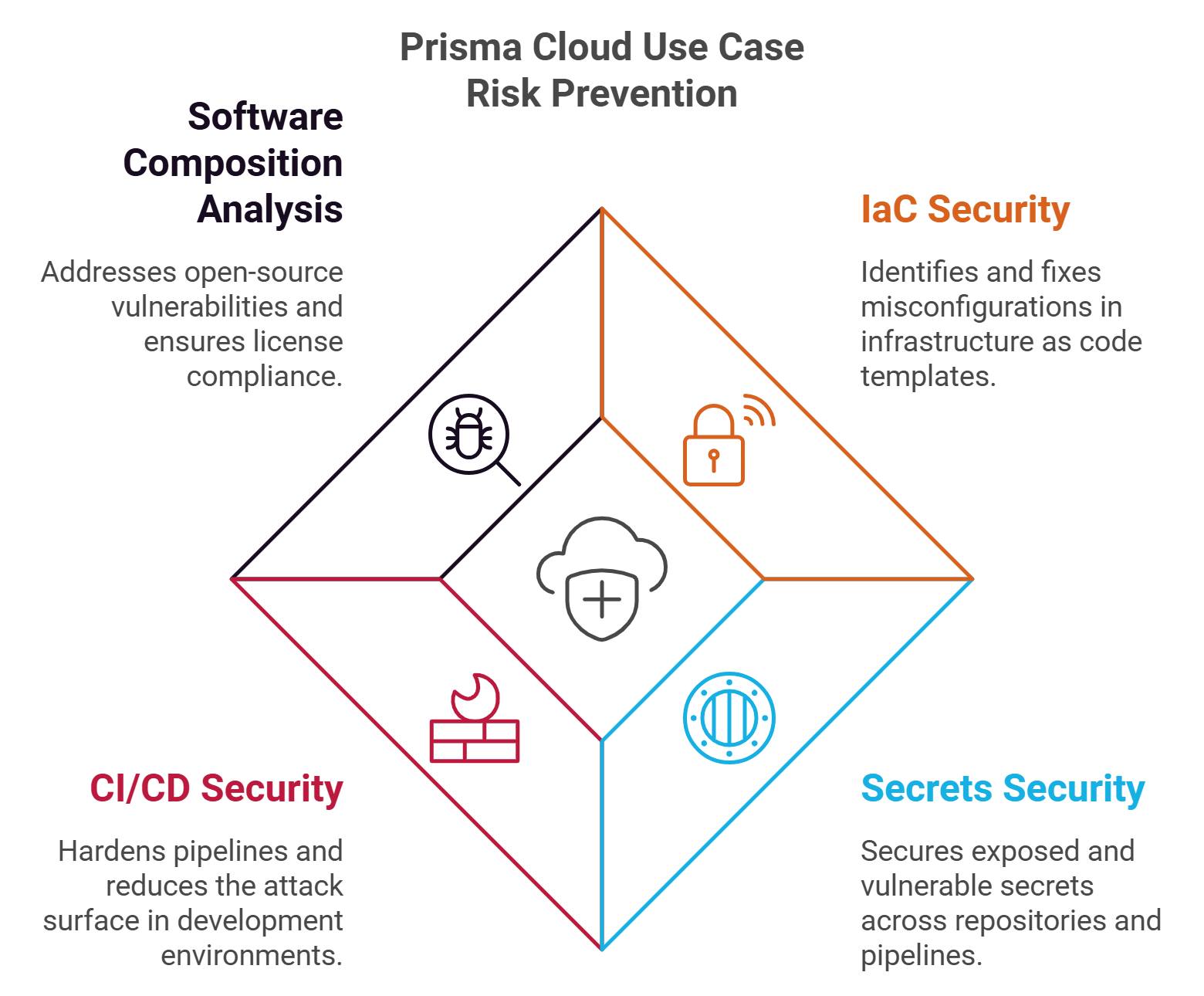
Risk Prevention Shift-left and secure applications by design. Prisma Cloud integrates with engineering ecosystems to prevent risks and misconfigurations from entering production, offering:
- IaC Security: Identify and fix misconfigurations in Terraform, CloudFormation, ARM, Kubernetes, and other IaC templates.
- Secrets Security: Find and secure exposed and vulnerable secrets across all files in repositories and CI/CD pipelines.
- CI/CD Security: Harden CI/CD pipelines, reduce the attack surface, and protect your application development environment.
- Software Composition Analysis: Address open-source vulnerabilities and license compliance issues with context-aware prioritization.
Prisma® Cloud Use Case - Visibility and Control
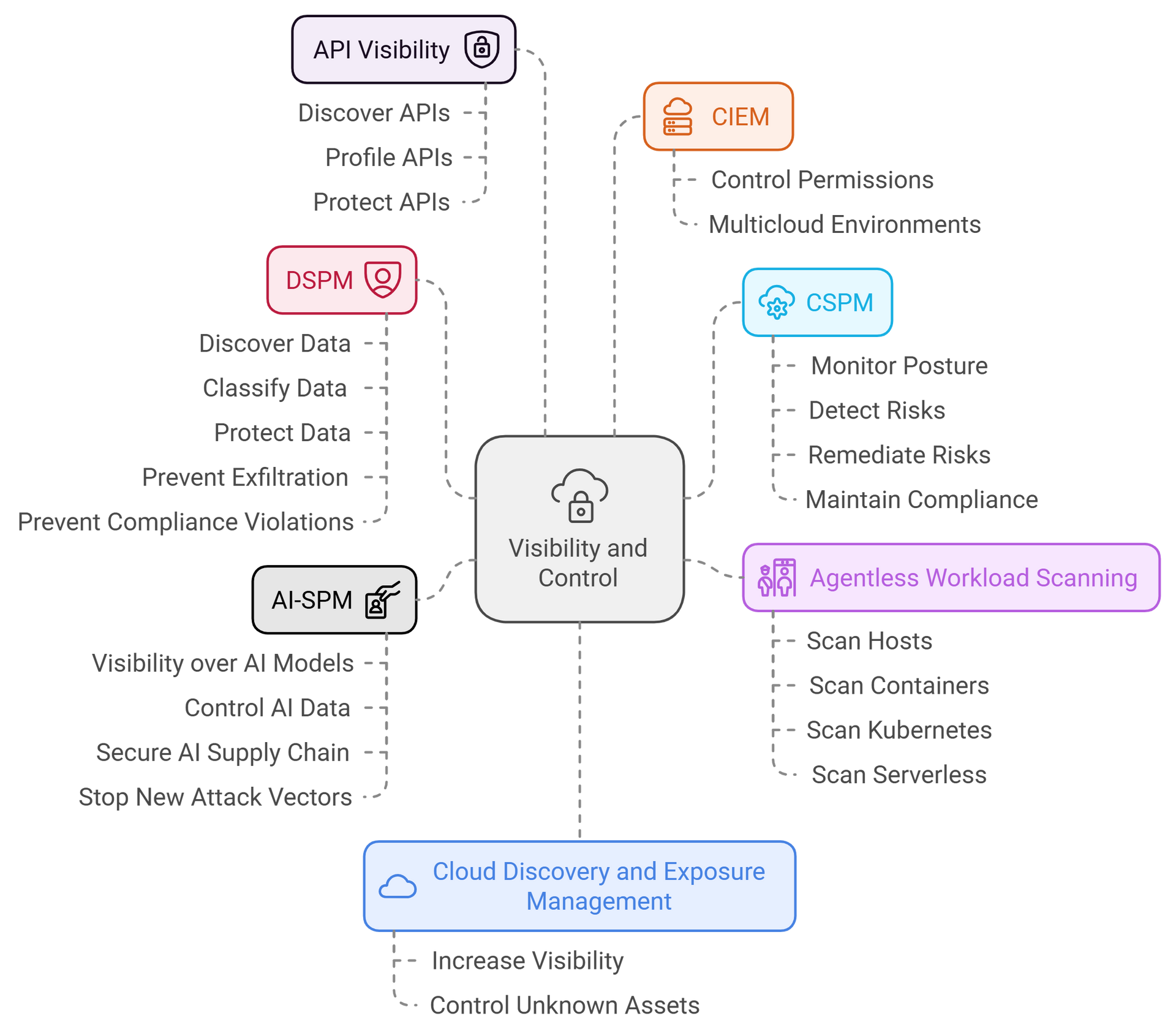
Visibility and Control
Gain continuous visibility and control over cloud misconfigurations, identity and access, data, vulnerabilities, and API endpoints across your cloud environment. Prisma Cloud secures cloud infrastructure, delivering:
- Cloud Security Posture Management (CSPM): Monitor posture, detect and remediate risks, and maintain compliance.
- Cloud Infrastructure Entitlement Management (CIEM): Gain control over permissions across multi-cloud environments.
- Agentless workload scanning: Scan hosts, containers, Kubernetes, and serverless for vulnerabilities and threats.
- API visibility: Discover, profile, and protect APIs across cloud-native applications. Protect against Layer 7, OWASP Top 10, API abuse, bad bots, DoS attacks, and more in any public or private cloud.
- Cloud discovery and exposure management: Increase visibility and control over unknown, unmanaged cloud assets exposed to the internet.
- Data Security Posture Management (DSPM): Discover, classify, and protect data in cloud environments. Prevent exfiltration and compliance violations.
- AI Security Posture Management (AI-SPM): Gain visibility and control over AI models, data, and the AI supply chain. Stop new attack vectors before they materialise.
Prisma Cloud Use Case - Runtime Protection
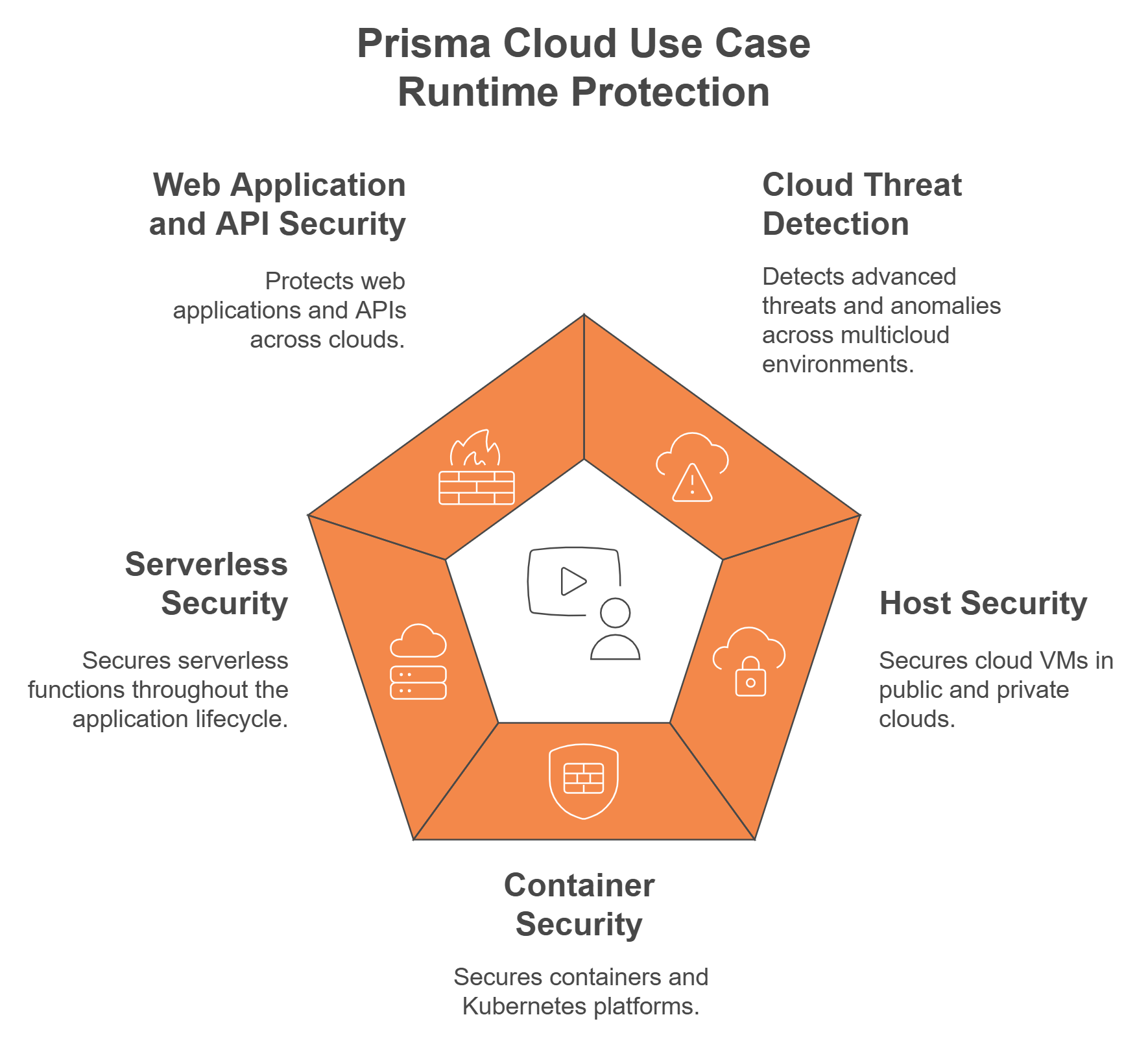
Runtime Protection
Block breaches in runtime and protect applications against attacks. Prisma® Cloud delivers threat protection across public and private clouds, including:
- Cloud Threat Detection: Detect advanced threats, zero-day attacks, and anomalies across multicloud environments.
- Host Security: Secure cloud VMs for any public or private cloud.
- Container Security: Secure containers and Kubernetes platforms on any public or private cloud.
- Serverless Security: Secure serverless functions across the full application lifecycle.
- Web Application and API Security: Protect web applications and APIs across any public or private cloud.
Code to Cloud Intelligence
Our unique approach is powered by Code to Cloud™ intelligence, connecting insights from the developer environment through application runtime to reduce risk and prevent breaches. Prisma Cloud contextualises alerts, prioritises critical risks, and offers remediation guidance.
- Visibility from Code to Cloud: Achieve comprehensive security visibility across engineering and cloud environments.
- Application Context: Create a complete application inventory to aid risk prioritisation.
- Attack Path Analysis: Find interrelated weaknesses and isolate exploitable attack vectors.
- Code to Cloud Remediation: Fix issues in code and the cloud from one place.

Industries and Markets Prisma Cloud Serves
Prisma® Cloud is designed to serve diverse industries, particularly those heavily invested in cloud transformation. These include:
Financial Services:
- Protects sensitive financial data and ensures compliance with APRA CPS 234 and PCI DSS.
- Provides continuous monitoring to safeguard against insider threats and unauthorised access.
Healthcare:
- Ensures compliance with healthcare regulations like HIPAA while protecting patient data stored in cloud environments.
- Secures IoT devices and medical systems connected to cloud platforms.
Government and Public Sector:
- Aligns with the Australian Cyber Security Centre’s (ACSC) Essential Eight strategies and SOCI requirements.
- Safeguards critical infrastructure and sensitive information.
Retail and E-Commerce:
- Secures consumer data and transactional systems.
- Mitigates risks of DDoS attacks and data breaches in high-traffic environments.
Technology and Software Development:
- Provides DevSecOps tools for secure application development and deployment.
- Offers runtime security for containers and Kubernetes environments.
Energy and Utilities:
- Ensures the security of operational technology (OT) and IoT devices connected to cloud systems.
- Protects critical infrastructure from sophisticated cyberattacks.
How Prisma Cloud Fits Within the Australian Cybersecurity Framework
Prisma Cloud aligns closely with Australia’s cybersecurity priorities, particularly as outlined by the Australian Cyber Security Centre (ACSC) and the Security of Critical Infrastructure Act (SOCI). Here's how:
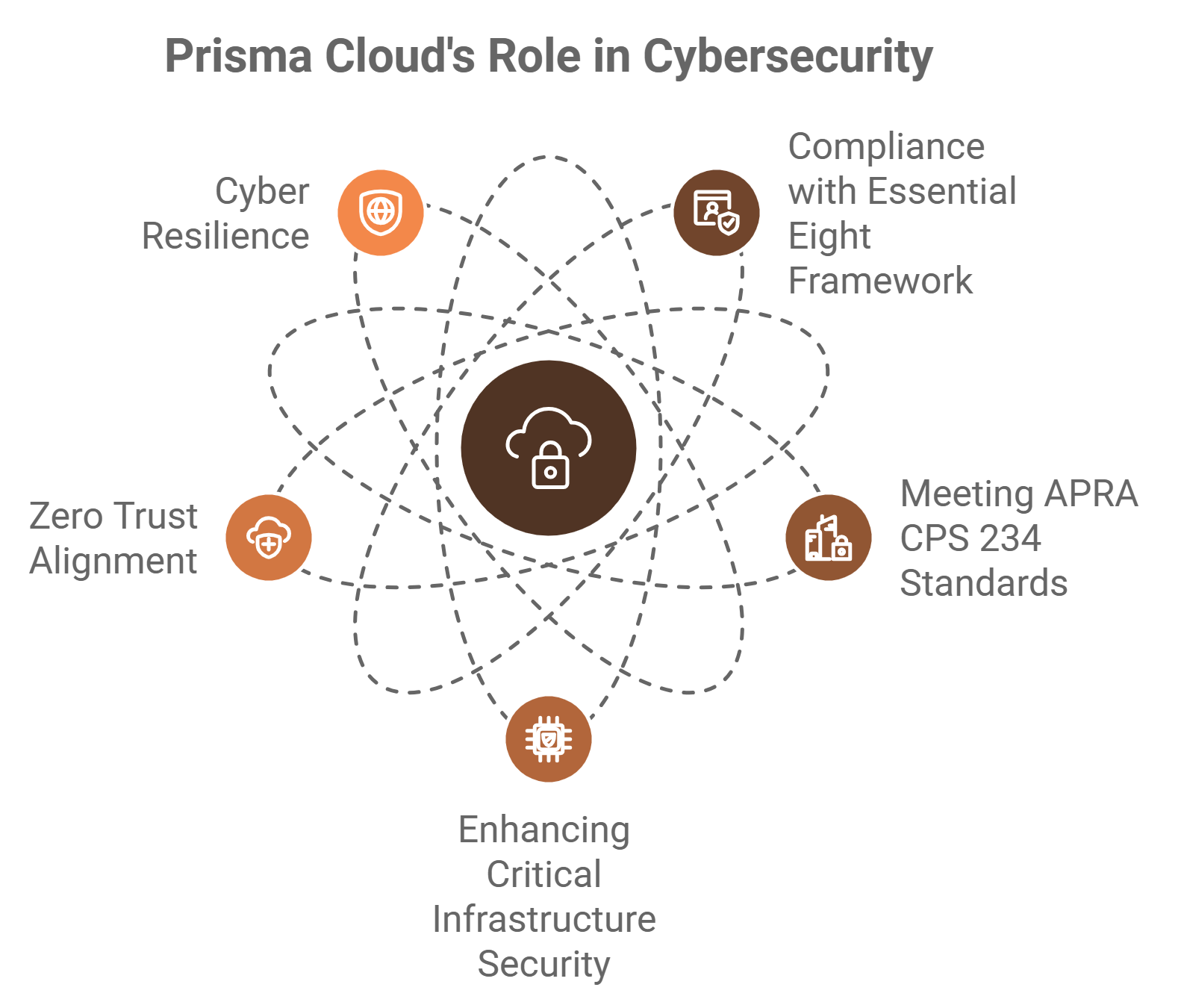
Compliance with the Essential Eight Framework:
- Automates compliance with the ACSC’s Essential Eight strategies, including patch management, application control, and privileged access management.
- Offers visibility into configuration drift and alerts for misalignments with best practices.
Meeting APRA CPS 234 Standards:
- Prisma Cloud helps financial institutions ensure information security and risk management.
- Provides real-time monitoring and reporting capabilities for audit readiness.
Enhancing Critical Infrastructure Security:
- Prisma Cloud safeguards workloads essential to critical infrastructure sectors such as energy, healthcare, and telecommunications.
- Aligns with SOCI Act requirements to proactively mitigate risks and vulnerabilities.
Zero Trust Alignment:
- Embodies Zero Trust principles by enforcing least-privilege access and securing cloud resources at every layer.
Cyber Resilience:
- Prisma Cloud automates threat detection and response, reducing the time to identify and mitigate breaches.
- Enables Australian organisations to maintain business continuity during cyber incidents.
Why Invest in Prisma Cloud?
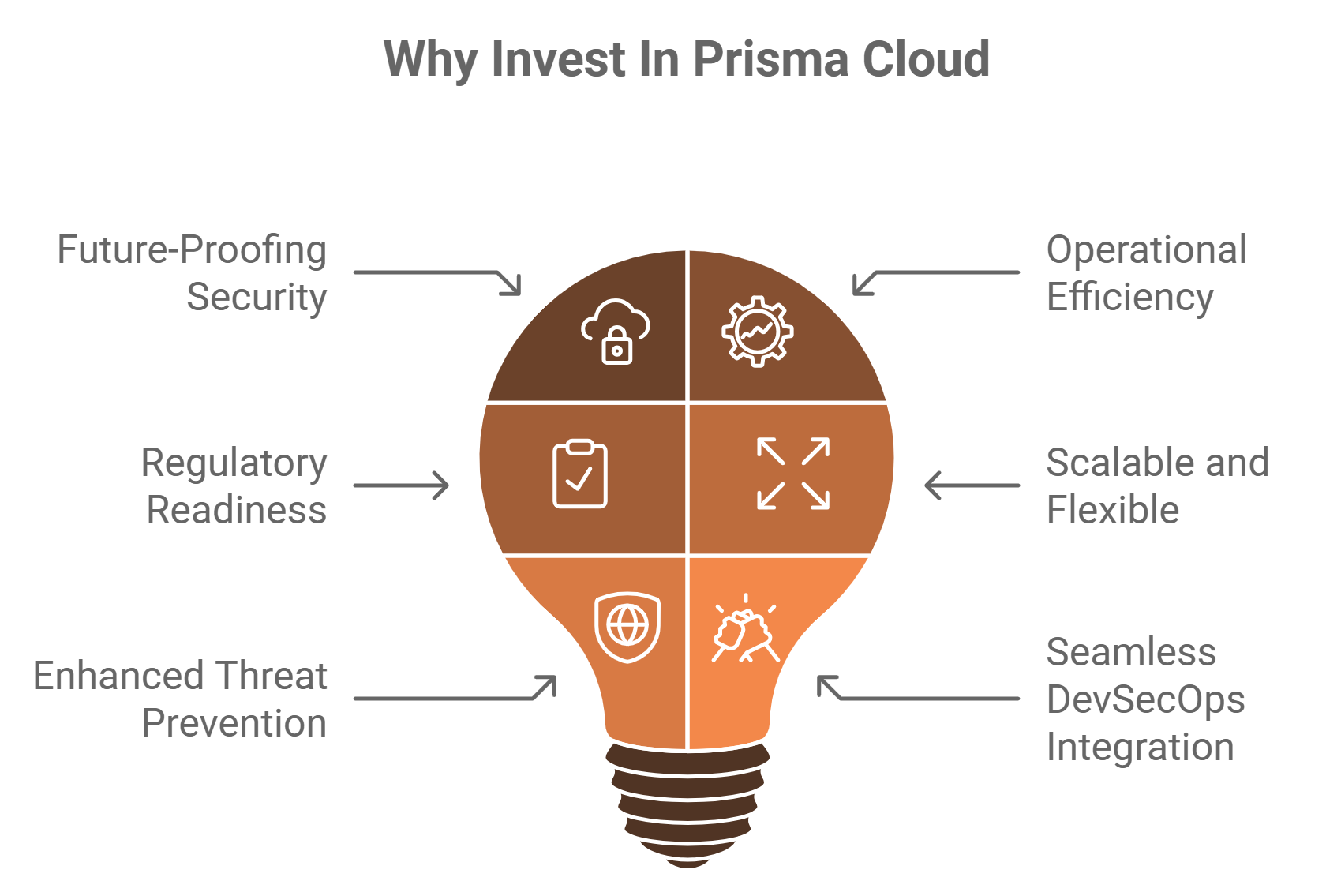
Future-Proofing Security:
- As Australian organisations embrace cloud transformation, Prisma Cloud ensures robust protection across hybrid and multi-cloud environments.
Operational Efficiency:
- Consolidates multiple security tools into a single platform, reducing complexity and management overhead.
- Identify and prevent vulnerabilities across the entire application lifecycle while prioritising risk for your cloud-native environments. Integrate vulnerability management into any CI process while continuously monitoring, identifying, and preventing risks to all workloads in your environment.
- Automates compliance checks and remediation, saving time and resources.
Regulatory Readiness:
- Ensures alignment with Australian cybersecurity standards, helping businesses avoid penalties and reputational damage. Easily implement and maintain compliance for Docker, Kubernetes, and Linux CIS Benchmarks, as well as external compliance regimes such as PCI, GDPR, NIST, and Istio. We also offer custom compliance checks that customers can create.
Scalable and Flexible:
- Adapts to the evolving needs of businesses, whether scaling workloads or integrating new technologies.
- Integrate security into the development process to find and fix issues in your registries and images before they make it into production.
Enhanced Threat Prevention:
- Leverages AI and machine learning to provide proactive and adaptive security, protecting against advanced threats.
Seamless DevSecOps Integration:
- Bridges the gap between development, security, and operations teams to ensure secure application delivery.
- Establish and monitor access control measures for cloud workloads and cloud-native applications across underlying hosts, Docker, and Kubernetes while integrating with identity and access management (IAM) and secrets management tools, along with other core technologies.
Prisma® SD-WAN
Palo Alto Networks' Prisma® SD-WAN is a software-defined wide area network (SD-WAN) solution designed to provide secure, reliable, and optimised connectivity for branch offices, remote sites, and hybrid work environments. It simplifies the management of network infrastructure by using intelligent automation and cloud-based management while ensuring high performance and security.
Unlike traditional WAN solutions, Prisma® SD-WAN integrates seamlessly with Palo Alto Networks’ broader cybersecurity ecosystem, including Prisma® Access for Secure Access Service Edge (SASE), enabling a unified, secure, and agile networking experience.
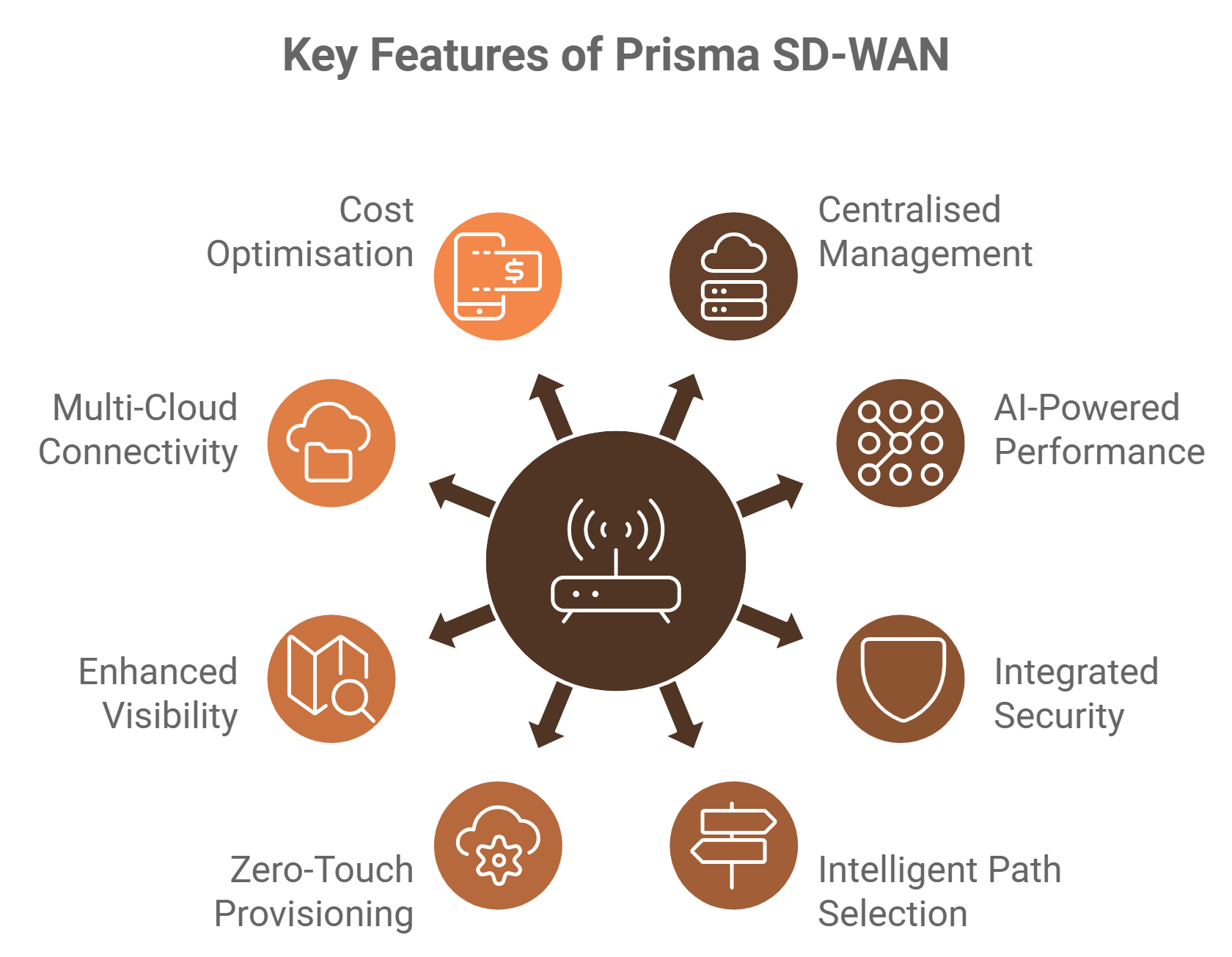
Key Features of Prisma SD-WAN
Centralised Cloud Management:
- Offers a cloud-delivered interface to manage all branch and edge networks.
- Simplifies deployment, monitoring, and updates across distributed sites.
AI-Powered Application Performance:
- Ensures reliable and optimised application delivery with real-time traffic steering.
- Uses machine learning to prioritize business-critical applications over recreational traffic.
Integrated Security with Prisma Access:
- Seamlessly integrates with Prisma Access to deliver Secure Access Service Edge (SASE) functionality.
- Provides consistent security across all network edges, reducing complexity.
Intelligent Path Selection:
- Uses dynamic path selection to route traffic based on performance metrics such as latency, jitter, and packet loss.
- Optimises bandwidth usage and ensures high-quality user experiences.
Zero-Touch Provisioning:
- Simplifies branch office deployments with automated provisioning and configuration.
- Minimises the need for on-site IT staff.
Enhanced Visibility and Analytics:
- Provides granular insights into network performance, application usage, and potential issues.
- Uses analytics to optimize network behavior and proactively address problems.
Multi-Cloud Connectivity:
- Enables direct, secure connections to public and private cloud providers like AWS, Azure, and Google Cloud.
- Reduces the complexity and cost of connecting to multi-cloud environments.
Cost Optimisation:
- Supports hybrid WAN architectures, combining MPLS, broadband, and LTE for cost-effective connectivity.
- Eliminates reliance on expensive legacy WAN solutions.
Use Cases for Prisma SD-WAN
Secure and Optimised Branch Connectivity:
- Enables secure, high-performance connectivity for distributed branch offices.
- Ideal for retail chains, financial institutions, and healthcare providers with multiple locations.
Hybrid Workforce Enablement:
- Provides seamless, secure connectivity for remote workers accessing cloud or on-premises applications.
- Ensures consistent user experiences regardless of location.
Multi-Cloud Integration:
- Simplifies secure access to applications hosted across multiple cloud environments.
- Reduces latency and improves application performance for cloud-native workloads.
Retail and Point-of-Sale (POS) Systems:
- Secures and optimises POS transactions in retail environments with multiple branch locations.
- Protects sensitive customer data and ensures consistent transaction processing.
Operational Technology (OT) Security:
- Secures and optimises connections for industrial IoT devices and operational technology in manufacturing or energy sectors.
- Reduces downtime and enhances operational efficiency.
Healthcare Network Reliability:
- Supports telemedicine and other healthcare applications by providing reliable, secure connectivity for remote clinics and mobile units.
How Prisma SD-WAN Fits Within the Australian Cybersecurity Framework
Prisma SD-WAN aligns with the Australian Cyber Security Centre’s (ACSC) strategies and regulatory frameworks by addressing critical security and connectivity requirements:
1. Compliance with the ACSC Essential Eight:
- Provides robust security controls, including encryption for data in transit and Zero Trust principles, reducing the risk of unauthorised access and data breaches.
- Enhances patch management by ensuring devices and systems are updated remotely via centralised cloud management.
2. Alignment with APRA CPS 234 Standards:
- Prisma SD-WAN helps financial institutions meet APRA CPS 234 requirements by securing sensitive data and ensuring high availability of critical systems.
- Offers advanced monitoring and threat detection capabilities, ensuring timely identification and mitigation of risks.
3. Supporting the Security of Critical Infrastructure Act (SOCI):
- Ensures the resilience of critical infrastructure networks by delivering secure, optimised, and redundant connectivity.
- Provides visibility into network performance, supporting proactive risk management in critical sectors like healthcare, energy, and telecommunications.
4. Zero Trust Network Access (ZTNA):
- Embeds ZTNA principles to authenticate users and devices before granting network access.
- Reduces the attack surface and improves security posture across hybrid and distributed environments.
5. Cyber Resilience and Business Continuity:
- Prisma SD-WAN’s dynamic path selection ensures uninterrupted connectivity during network outages or disruptions.
- Enhances cyber resilience by automating failover processes and maintaining high-quality application performance.
Why Invest in Prisma SD-WAN?
1. Enhanced Security:
- Prisma SD-WAN integrates tightly with Prisma Access, delivering consistent security across all edges of the network.
2. Simplified Management:
- Centralised cloud-based management reduces the complexity of managing distributed networks, saving time and resources.
3. Cost Efficiency:
- Hybrid WAN architectures lower costs compared to traditional MPLS-only solutions.
4. Future-Ready Architecture:
- Built for cloud-first and hybrid environments, ensuring scalability and adaptability for evolving business needs.
5. Regulatory Compliance:
- Meets Australian regulatory requirements like APRA CPS 234 and SOCI Act, reducing compliance risks.
6. Optimised User Experience:
- AI-driven traffic steering and dynamic path selection ensure high-performance connectivity for business-critical applications.
Prisma® SaaS
Prisma® SaaS by Palo Alto Networks is a Next-Generation Cloud Access Security Broker (CASB) designed to provide visibility, compliance, and security for Software-as-a-Service (SaaS) applications. As organisations increasingly adopt SaaS platforms like Microsoft 365, Google Workspace, Salesforce, and Slack, Prisma® SaaS helps them secure sensitive data, monitor user activities, and prevent potential threats.
Prisma® SaaS offers a seamless blend of inline and API-based protection, giving businesses the tools to safeguard both sanctioned and unsanctioned applications, manage data loss risks, and ensure compliance with regulations.
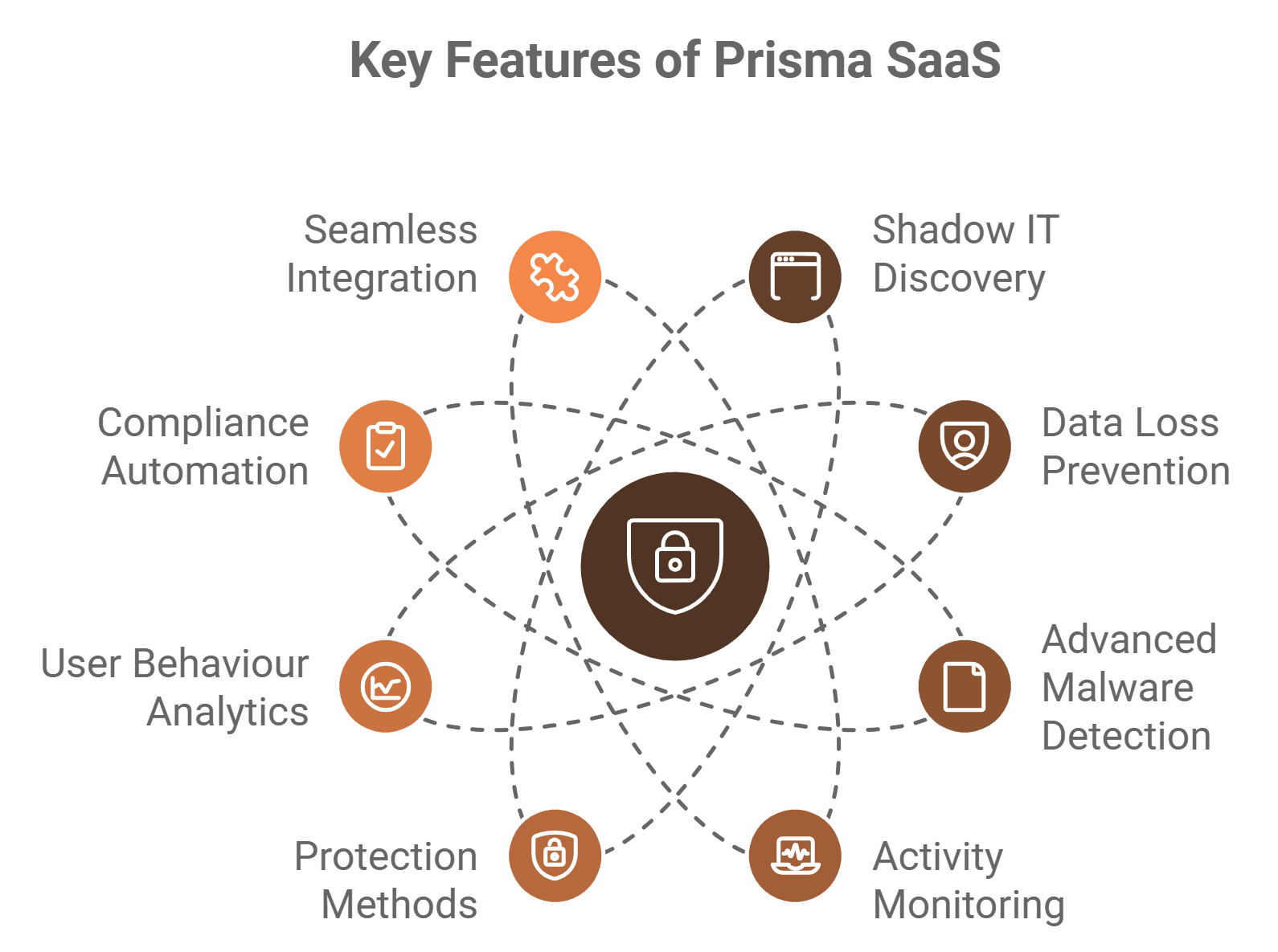
Key Features of Prisma® SaaS
Shadow IT Discovery and Risk Management:
- Identifies and assesses unsanctioned SaaS applications used by employees (shadow IT).
- Provides risk ratings and recommendations for mitigating potential threats.
Data Loss Prevention (DLP):
- Detects and prevents the sharing or leakage of sensitive data across SaaS platforms.
- Includes predefined compliance templates for regulations like GDPR, PCI DSS, and APRA CPS 234.
Advanced Malware Detection:
- Leverages Palo Alto Networks’ Advanced Threat Prevention to scan for and block malware in SaaS environments.
- Integrates with WildFire for zero-day threat detection.
Comprehensive Activity Monitoring:
- Tracks user activity across SaaS platforms, enabling granular auditing and forensic analysis.
- Detects anomalies such as unusual login patterns or excessive data downloads.
Inline and API-Based Protection:
- Inline protection monitors real-time traffic to SaaS applications, enforcing access and security policies.
- API-based protection secures data stored within SaaS applications, such as files and emails.
User Behaviour Analytics (UBA):
- Uses AI-driven analytics to detect suspicious activities that may indicate insider threats or compromised accounts.
- Offers automated alerts and recommendations for remedial actions.
Compliance Automation:
- Helps organisations meet industry-specific compliance standards by monitoring data usage and enforcing policies.
- Offers detailed compliance reporting to satisfy regulatory requirements.
Seamless Integration:
- Integrates with Palo Alto Networks’ broader cybersecurity ecosystem, including Prisma® Access and Cortex, for unified security management.
Use Cases for Prisma® SaaS
Shadow IT Risk Mitigation:
- Identifies unsanctioned SaaS applications that could expose sensitive data to unauthorized users or external threats.
- Provides organisations with visibility and control over shadow IT.
Data Loss Prevention (DLP) Across SaaS Platforms:
- Monitors and enforces policies to prevent sensitive data from being shared or leaked via SaaS applications.
Securing Collaboration Tools:
- Protects collaboration platforms like Google Workspace and Microsoft 365 from data breaches and malware attacks.
- Ensures secure file sharing and document management.
Regulatory Compliance Management:
- Ensures SaaS applications comply with data protection laws like GDPR, CCPA, and APRA CPS 234 by monitoring and managing sensitive data.
Insider Threat Detection:
- Identifies anomalous user behavior that could indicate malicious activity or compromised credentials.
Incident Response and Forensics:
- Enables granular auditing of user actions for incident investigation and compliance reporting.
How Prisma® SaaS Fits Within the Australian Cybersecurity Framework
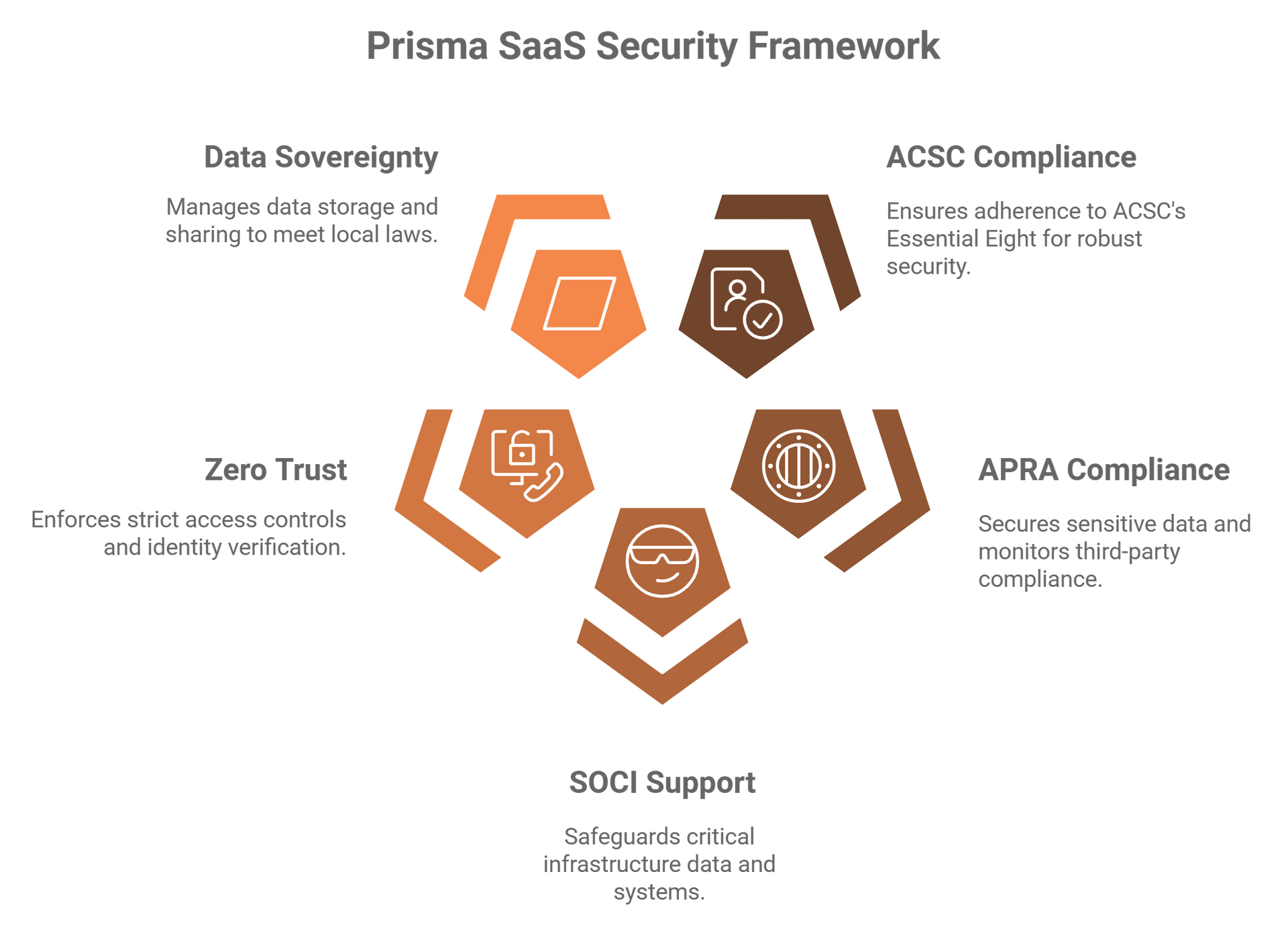
Prisma SaaS aligns with the Australian Cyber Security Centre’s (ACSC) strategies and regulations by addressing key challenges in SaaS adoption and security:
Compliance with the ACSC Essential Eight:
- Implements strong access controls and DLP to mitigate risks associated with unauthorized data sharing.
- Supports patch management by monitoring SaaS application updates and configurations.
Meeting APRA CPS 234 Requirements:
- Secures sensitive data stored in SaaS applications for financial institutions.
- Monitors third-party SaaS providers to ensure they comply with APRA CPS 234 obligations.
Supporting the Security of Critical Infrastructure Act (SOCI):
- Protects data and systems in critical industries using SaaS platforms for collaboration and operations.
- Monitors and mitigates risks to sensitive data in critical infrastructure sectors.
Zero Trust Enablement:
- Enforces Zero Trust principles by verifying user identities and monitoring access to SaaS applications.
- Ensures only authorised users can access sensitive data within SaaS environments.
Data Sovereignty and Privacy:
- Ensures Australian businesses comply with local data sovereignty requirements by monitoring and managing how data is stored and shared across SaaS platforms.
Why Invest in Prisma® SaaS?
Enhanced SaaS Visibility
Identifies and manages shadow IT, providing complete oversight of SaaS application usage.
Robust Data Protection
Prevents data breaches and enforces compliance with stringent data protection laws.
Threat Prevention
Detects and blocks advanced threats like zero-day malware and phishing attempts targeting SaaS applications.
Regulatory Compliance
Helps organisations meet Australian regulatory requirements, including APRA CPS 234 and SOCI Act obligations.
Operational Efficiency
Automates compliance reporting and reduces the time spent on manual data audits.
Seamless Integration
Complements other Palo Alto Networks products like Prisma Access and Cortex, creating a unified security framework.
Scalability and Flexibility
Adapts to the growing use of SaaS platforms, ensuring security as businesses expand their digital footprint.
Contact us today
Palo Alto Networks’ Prisma® suite offers a comprehensive set of cloud-based security solutions tailored to meet the needs of modern organizations. Prisma® solutions are designed to protect applications, data, and users across hybrid and multi-cloud environments while enabling secure and efficient network connectivity. The key solutions include:
Prisma® Access (SASE)
- Combines secure access with cloud-delivered network services to enable Zero Trust principles.
- Ideal for securing remote workforces and branch offices.
Prisma® Cloud (CNAPP)
- Provides full-lifecycle security for cloud-native applications, including containers, Kubernetes, and serverless architectures.
- Ensures compliance, visibility, and runtime protection for cloud workloads.
Prisma® SD-WAN
- Optimises branch connectivity with software-defined networking and secure cloud integration.
- Improves application performance and simplifies management.
Prisma® SaaS (Next-Gen CASB)
- Secures SaaS applications by preventing data loss, monitoring user activity, and detecting shadow IT.
- Provides both inline and API-based protection for cloud applications.
If you are looking to
- Secure your environment across hybrid and multi-cloud, on-premises data centers and SaaS applications.
- Want to implement zero-trust principles to minimise risk and prevent unauthorised access.
- Want improved visbility and control of network traffic, application usage, and workload and environments.
- Want to leverage AI for advanced threat protection against malware, ransomware and zero day threats.
- Want to align with the Australian Cybersecurity Framework and achieve compliance in security of critical infrastructure and legislations
- Would like to increase operational efficiency in the managing networks and reducing down time
- Would like a solution that seamlessly integrates and scales as your organisation changes.
Call us today for a confidential discussion, for special pricing and for more information on 1300 019 919.











