Best Practices for Cloud Network Security
Insights for 2024 and Beyond
The In an era where digital transformation drives business innovation, cloud computing has become an necessity in agility, scalability, and cost-efficiency. However, transitioning to cloud platforms has its unique security challenges, highlighting the importance of strong cloud network security measures.
Cloud network security is not a one-size-fits-all solution. It requires a comprehensive strategy tailored to the specific needs and risks of each organisation.
Our below guide provides best practices for cloud network security with actionable strategies and tips to help you enhance your organisation's network security in the cloud computing environment. This guide explores the best practices for securing cloud environments, integrating insights from trusted Australian resources and the Australian Government’s Cyber Security Centre (ACSC), alongside global perspectives.
The Cloud Security Landscape
The ACSC's annual Cyber Threat Report (2023–24) highlights that 43% of Australian cyber incidents now involve cloud environments. Key vulnerabilities include data breaches, misconfigured services, and insecure APIs. Globally, 93% of organisations acknowledge concerns about cloud security, while 70% of cloud breaches are linked to misconfiguration issues.

15 Best Practices for Cloud Network Security
1. Conduct a Cloud-Specific Risk Assessment
- Identify sensitive data and assess potential threats.
- Evaluate third-party and cloud service provider (CSP) security policies.
- Ensure compliance with regulations such as the Australian Privacy Act 1988 or GDPR for global operations.
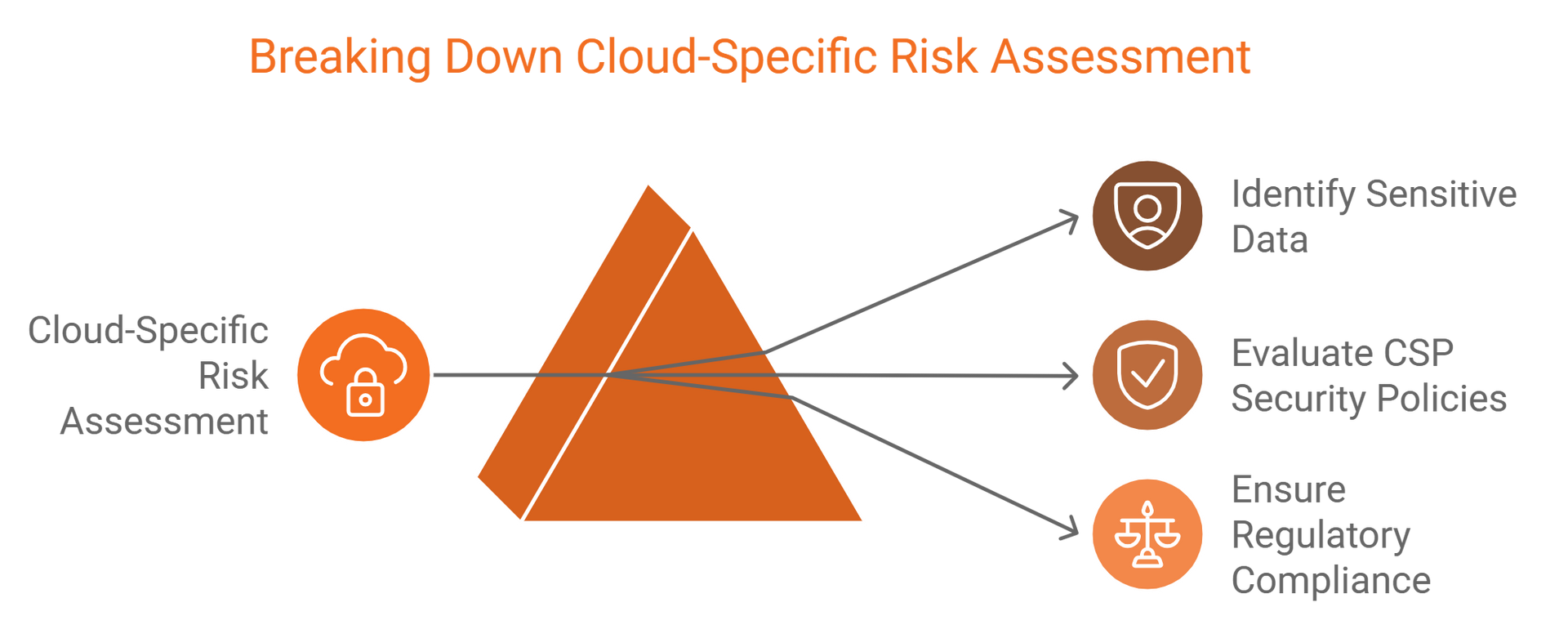
2. Select the Right Cloud Service Model
Understand the shared responsibility model for IaaS, PaaS, and SaaS environments. For instance, in SaaS solutions, user responsibilities often focus on access control and data protection.
The shared responsibility model is a cornerstone of cloud security. It outlines the division of security responsibilities between a cloud service provider and the customer. Knowing these roles helps in safeguarding cloud infrastructure effectively.
Cloud providers typically manage the security of the cloud itself, including its infrastructure and physical storage facilities. Customers, on the other hand, are responsible for managing security in the cloud, focusing on their data, applications, and user access. Grasping this model ensures that both parties work together to maintain a enhanced security posture.
3. Strengthen Access Control Mechanisms
- Multi-Factor Authentication (MFA) can reduce account compromise risks by 99.9%, according to Microsoft.
- Role-based access ensures only authorised users handle sensitive systems.
Implementing Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds a necessary security layer by requiring multiple verification methods. This process effectively reduces unauthorised access risks, as it provides a critical barrier even if passwords are compromised.
By combining something the user knows (password), something they have (a phone or token), and sometimes something they are (fingerprint), MFA strengthens security. Its implementation is a strategic move for organisations looking to enhance their cloud network security. Deploying MFA across all access points is crucial in safeguarding sensitive data and services within the cloud. This method ensures a stronger defense against cyber threats.
Identity and Access Management (IAM) Strategies
Identity and Access Management (IAM) is critical for securing cloud networks. It involves managing who has access to cloud resources and what they can do with those resources. Effective IAM strategies restrict access to ensure only authorised users can perform certain actions.
A key component of IAM is implementing strict role-based access controls (RBAC). This limits user permissions based on their role within an organisation, reducing the risk of unauthorised data access or modifications.
Here are some best practices for IAM in cloud environments:
- Implement strong authentication methods like MFA.
- Regularly review and update user roles and permissions.
- Use IAM tools to automate user management tasks.
Consistent monitoring of IAM configurations is important. Detecting and addressing misconfigurations promptly helps maintain strong security measures. Continuous evaluation ensures IAM strategies evolve as security needs change, protecting network security in cloud computing environments.
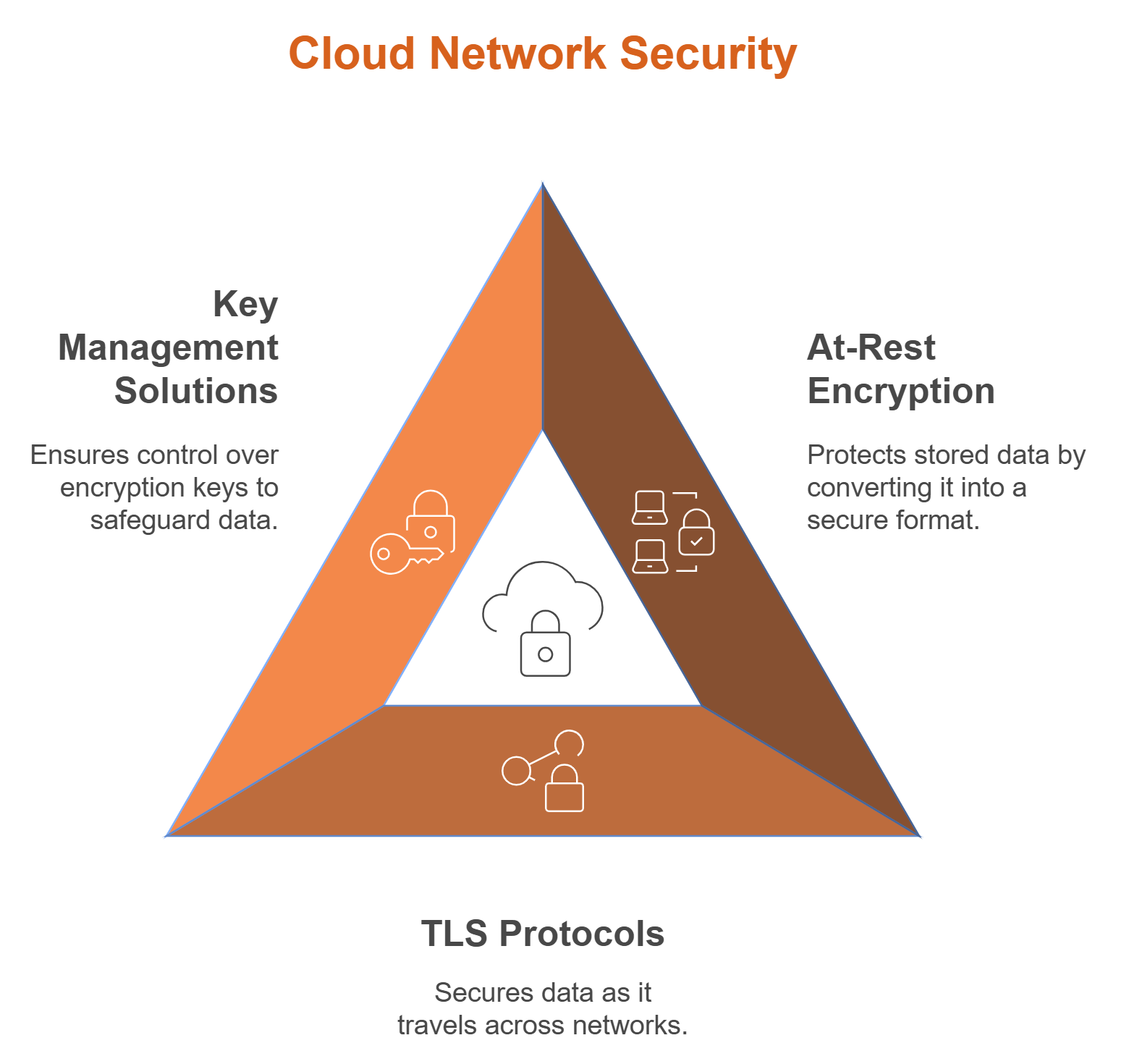
4. Encrypt Data Across the Cloud
- At-rest encryption ensures stored data security, while TLS protocols secure data in transit.
- The ACSC recommends implementing secure encryption key management solutions to maintain control over sensitive data.
Encryption is important for securing data in the cloud. It transforms readable data into an unreadable format, protecting it from unauthorised access. This practice plays an essential role in protecting sensitive information.
The use of encryption in cloud computing ensures that both data at rest and data in transit remain secure. Modern encryption technologies utilise advanced algorithms to keep data confidential. This approach is complemented by effective key management, which is vital for encryption's success.
Incorporating encryption into a cloud security strategy offers several benefits:
- Protects sensitive information from unauthorised access.
- Ensures compliance with data protection regulations.
- Builds trust with customers by ensuring data privacy.
Encrypting Data at Rest
Data at rest includes any data that is stored but not being accessed or moved. Encryption at this stage is important to prevent unauthorised access. It ensures that even if data is physically compromised, it remains unreadable.
Employing strong encryption algorithms and key management is essential to protect data at rest. This approach enhances security and ensures compliance with various industry standards. Effective encryption provides peace of mind that stored data remains confidential.
Encrypting Data in Transit
Data in transit refers to data actively moving from one location to another, such as across the internet. Encryption of this data ensures its confidentiality during transfer. It protects against interception by unauthorised parties.
To secure data in transit, organisations should use protocols like TLS or VPNs. These technologies secure data during its journey, preventing eavesdropping and tampering. Ensuring encrypted communication is key to safeguarding data integrity across networks.
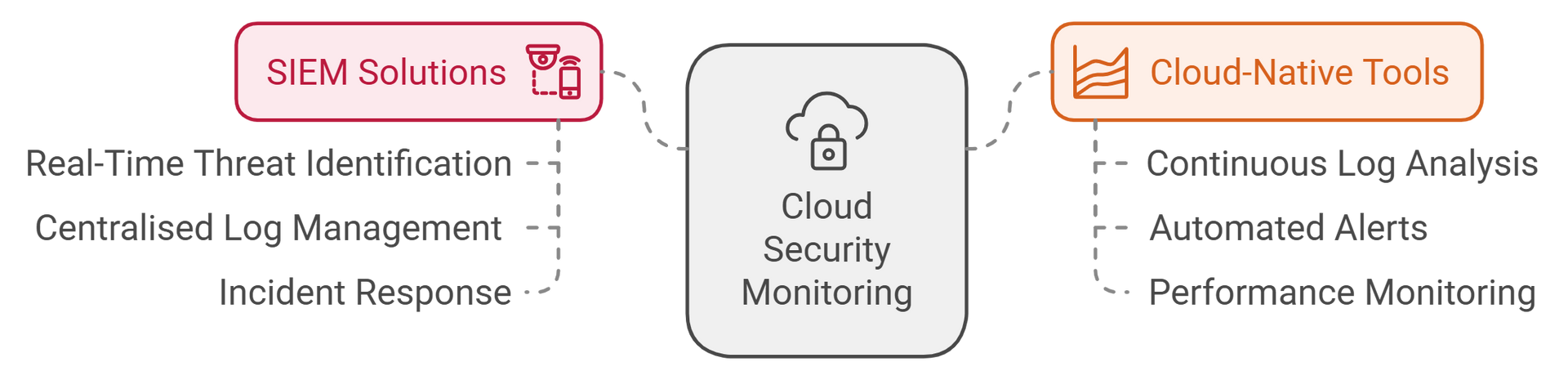
5. Monitor Cloud Activities with Advanced Tools
- Adopt Security Information and Event Management (SIEM) solutions to identify threats in real-time.
- The ACSC encourages leveraging cloud-native monitoring tools for continuous log analysis.
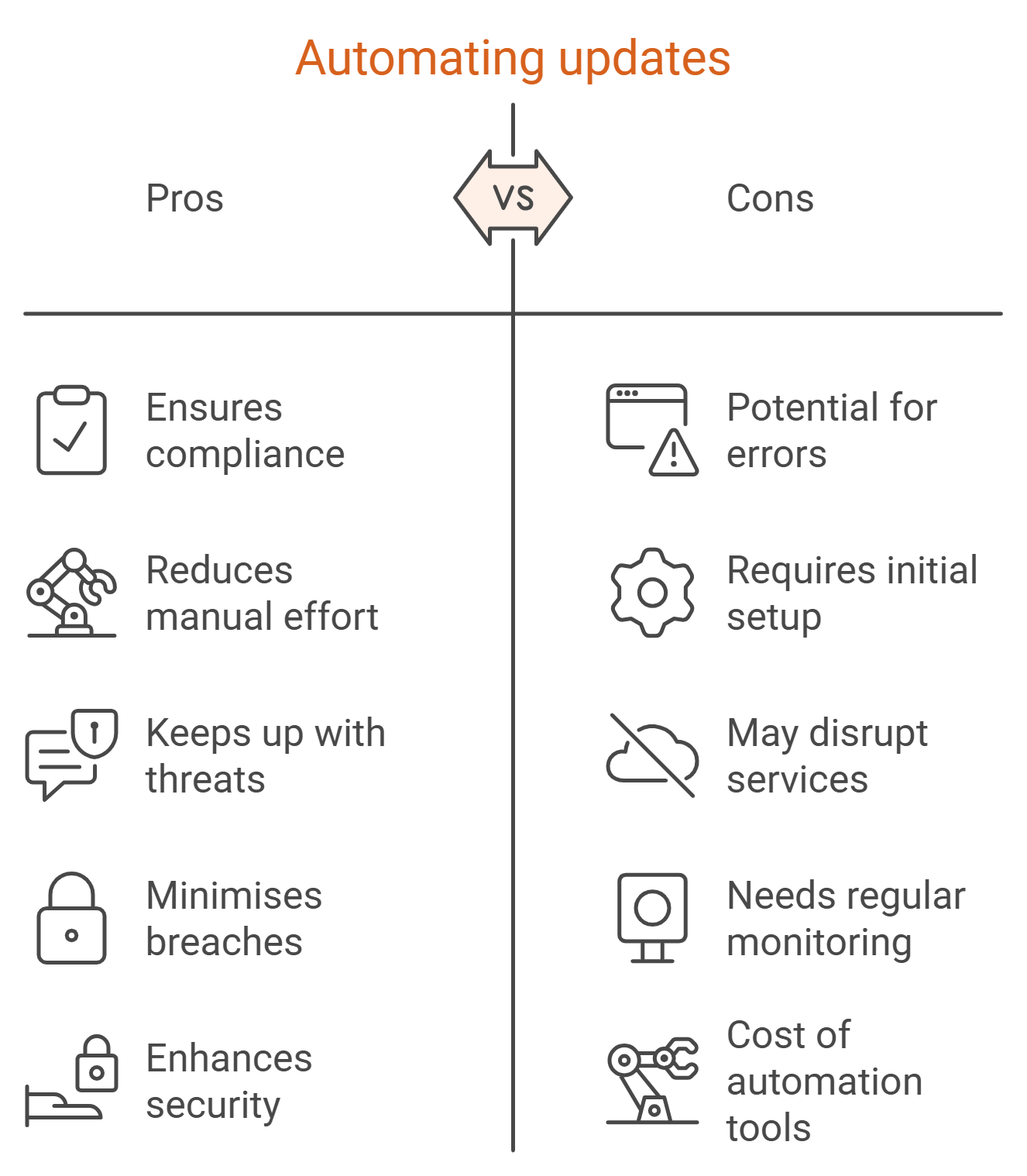
6. Apply Regular Patches and Updates
Unpatched vulnerabilities are a leading cause of breaches. Automating updates ensures compliance with evolving threat landscapes.
Patch management is a key aspect of cloud network security. It ensures that software systems remain up-to-date and protected against known vulnerabilities. Timely application of patches helps prevent attackers from exploiting security gaps.
Vulnerability scanning identifies potential weaknesses in cloud infrastructure. Regular scans are essential for maintaining stronger security. They allow organisations to proactively address issues before they are exploited. This dual approach of patch management and scanning is vital for strong network protection.
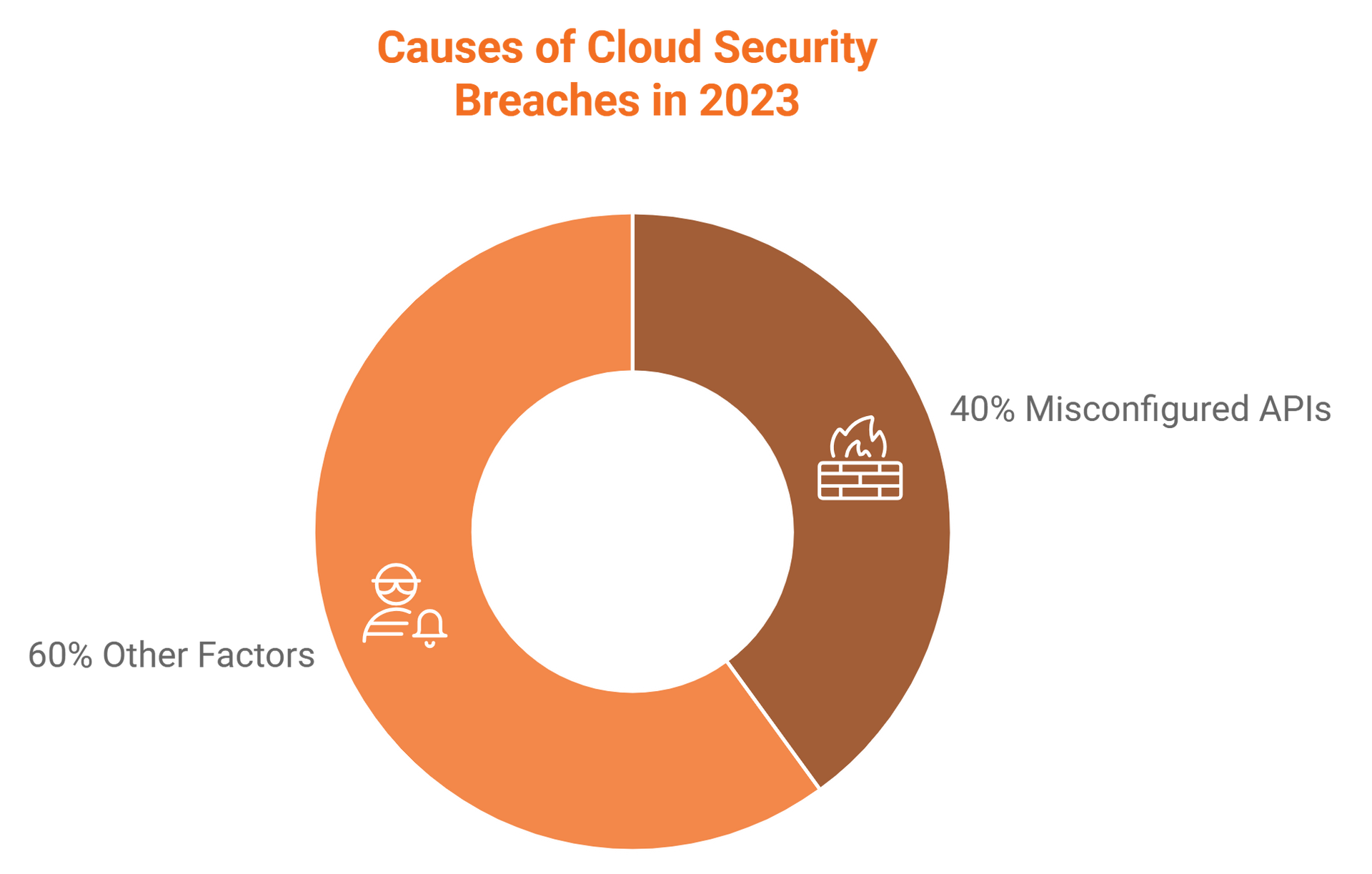
7. Secure APIs
Misconfigured APIs accounted for 40% of cloud security breaches in 2023. Implement API gateways and authentication mechanisms to mitigate risks.
8. Segment Cloud Networks
- Create Virtual Private Clouds (VPCs) for isolated workloads.
- Utilise micro-segmentation to restrict unnecessary lateral movement across environments.
Network Segmentation and Micro-Segmentation
Network segmentation is an important practice in network security in cloud computing. By dividing a network into smaller segments, you can limit the spread of potential breaches. This approach helps isolate sensitive data and applications, providing an additional layer of protection.
Micro-segmentation takes this concept further by applying security policies to individual workloads. This precision enables tailored protection based on specific network traffic patterns. Implementing micro-segmentation helps ensure robust cloud security by limiting unauthorised access and preventing attackers from moving laterally within the network. This granular control fosters stronger network protection.
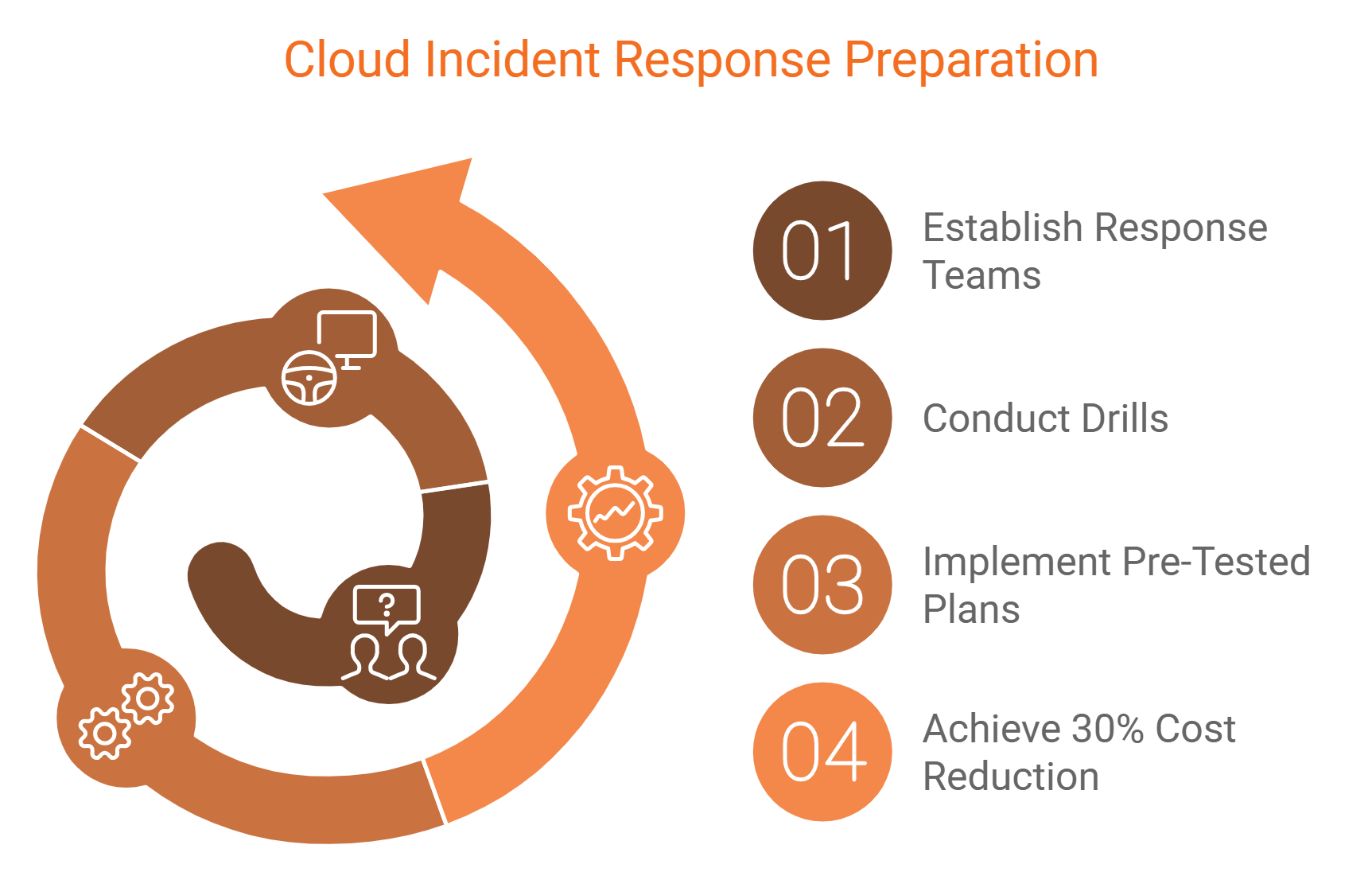
9. Develop a Cloud Incident Response Plan
Establish response teams and conduct drills. According to the ACSC, organisations with pre-tested plans reduce breach costs by 30%.
Incident response is a critical component of any effective cloud security strategy. A well-defined plan enables organisations to act quickly during a security breach, minimising damage. It outlines roles, responsibilities, and procedures to ensure a swift reaction to incidents.
To build a plan, begin by identifying potential threats and vulnerabilities specific to your cloud environment. Conduct regular drills to test the plan's effectiveness and make necessary adjustments. Continuous improvement of the incident response plan ensures readiness and resilience in facing new and evolving threats.
10. Enhance Employee Awareness
Training programs targeting phishing and social engineering threats can significantly lower human-error-driven incidents.
Employees are often the first line of defense in maintaining cloud security. Their awareness of potential threats can reduce security risks significantly. Training programs play a crucial role in preparing staff for recognising and preventing security breaches.
Regular training sessions should focus on educating employees about the latest security threats and safe online practices. This not only strengthens the organization's security posture but also empowers employees to act as security advocates. By instilling a proactive security mindset, organizations can better protect their cloud environments from human-related vulnerabilities.
11. Leverage Security Tools and Solutions
- Cloud Access Security Brokers (CASBs) enforce data compliance policies.
- Intrusion Detection Systems (IDS) prevent unauthorised access attempts.
Utilising Cloud Access Security Brokers (CASBs)
Cloud Access Security Brokers (CASBs) serve as an essential security bridge between cloud service consumers and providers. They help organisations maintain compliance and enhance data security within cloud environments. CASBs provide visibility into cloud usage and enable the enforcement of security policies.
By monitoring all cloud traffic, CASBs protect sensitive information from unauthorised access or breaches. They deliver advanced features like real-time data protection, threat detection, and encryption, tailored to secure cloud applications effectively. Employing CASBs is a smart step towards ensuring comprehensive network protection and maintaining cloud infrastructure security.
Leveraging Artificial Intelligence for Threat Detection and Response
Artificial Intelligence (AI) plays a pivotal role in modern cloud security. AI enhances threat detection by analysing vast amounts of data for patterns indicating potential breaches. This technology enables quicker identification of threats, reducing response time significantly.
Moreover, AI-driven tools can automate many aspects of threat response. They provide actionable insights, ensuring timely interventions before incidents escalate. By incorporating AI into your security strategy, you can greatly improve your cloud network's resilience against sophisticated attacks and evolving threats.
Continuous Monitoring, Logging, and Threat Intelligence
Continuous monitoring is crucial for maintaining security in cloud environments. It involves regularly checking systems for potential vulnerabilities and suspicious activities. By doing so, organisations can address security issues promptly.
Logging is an essential component of cloud security, providing a detailed record of system activities. These logs help track unusual behavior or unauthorised access. They are vital for forensic analysis after a security incident, offering insights into the incident’s cause and impact.
Integrating threat intelligence improves the ability to predict and prevent attacks. Threat intelligence provides real-time information about emerging threats and vulnerabilities. This intelligence can be leveraged by security teams to refine security measures and build more resilient defenses.
- Benefits of Continuous Monitoring:
- Real-time alerts for fast response.
- Detailed logs for comprehensive analysis.
- Enhanced ability to anticipate threats.
Endpoint Security and the Importance of Device Management
In cloud environments, endpoint security is important for protecting devices that access cloud services. These endpoints are often entry points for cyber threats. Ensuring each device is secure prevents unauthorised access and potential data breaches.
Effective device management involves continuously monitoring and updating software on all connected devices. Patch management and software updates are vital components of device security. Regularly updating software minimises vulnerabilities, enhancing overall cloud security. Emphasising strong endpoint protection helps maintain data security in the cloud by securing every access point.
12. Ensure Regulatory Compliance
Regular compliance audits with Australian frameworks such as Essential Eight can strengthen organisational security.
13. Backup Data Regularly
Maintain offsite backups to safeguard business continuity in ransomware or disaster scenarios.
14. Vet Cloud Service Providers Thoroughly
Evaluate CSPs based on certifications like ISO 27001 or SOC 2. Ensure transparent policies around incident response capabilities.
15. Stay Updated with Emerging Threats
Utilise platforms like the Australian Cyber Security Centre Threat Intelligence Exchange and participate in security forums.
Australian Statistics and Regulatory Frameworks
- Essential Eight from the ACSC recommends foundational practices, including MFA, patching, and backups, to mitigate 85% of cyber threats.
- The Australian cloud market is forecasted to reach $14 billion by 2025, making security investments crucial for sustained growth.
Securing cloud environments is an evolving challenge. By aligning with the ACSC’s guidelines, implementing the strategies outlined, and enabling a security-first culture, businesses can reduce vulnerabilities and thrive in a digital-first economy. A proactive approach to cloud security not only safeguards data but also reinforces trust with clients and stakeholders.
For further insights, visit the Australian Government’s ACSC guidelines on cloud security: cyber.gov.au.
Konverge, a proudly Australian-owned and operated IT provider, partners with some of the most recognised brands to deliver exceptional IT and IT security solutions. Whether you're looking to enhance your current infrastructure or plan for future projects, our team is here to help. Reach out to us at sales@konverge.com.au or call 1300 019 919 today to discuss how we can support your success.



Latest Insights

Ask us anything
No matter what your question relates to, our IT specialists will be happy to help with any related enquiries.
We want to hear from you
Send us your details and we’ll get back to you to schedule a time to talk.
Contact us form Konverge footer
We will get back to you as soon as possible
Please try again later








