Palo Alto Networks PA-400 Series Next Generation Firewall
Network Security: PA-400 Series ML-Powered Next-Generation Firewall

This page aims to provide an overview of what Palo Alto Networks' PA-400 Series Next Generation Firewall (NGFW) entails.
About PA-400 Series
Palo Alto Networks PA-400 Series ML-Powered Next-Generation Firewalls, comprising the PA-460, PA-450, PA-445, PA-440, PA-415, PA-415-5G, PA-455, and PA-410, are designed to provide secure connectivity for distributed enterprise branch offices. The PA-400 series delivers ease of centralised management and provisioning with Panorama and Zero Touch Provisioning. Enables you to safely implement SD-WAN and delivers an exceptional end user experience by minimizing latency, jitter, and packet loss.
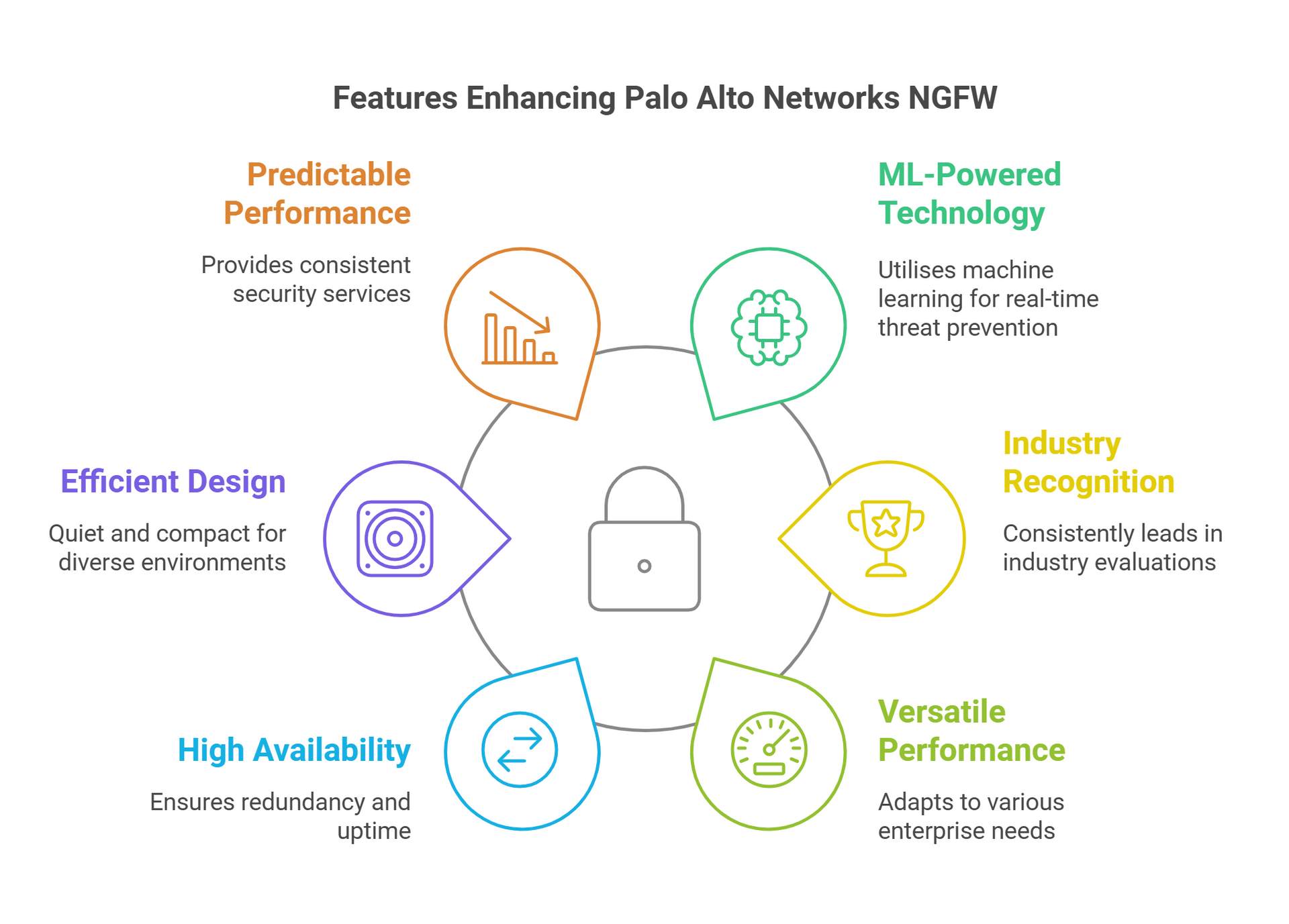
World’s First ML-Powered NGFW
- Pioneering real-time, AI-driven threat prevention.
Recognised Industry Leader
- Eleven-time Leader in the Gartner Magic Quadrant for Network Firewalls.
- Leader in the Forrester Wave: Enterprise Firewalls, Q1 2024.
Versatile Performance
- Designed for distributed enterprises with a broad lineup to meet varying performance needs.
- Includes desktop form factor options for compact security solutions.
High Availability
- Supports active/active and active/passive modes for redundancy and uptime.
Efficient and Quiet
- Features a silent, fanless design ideal for branch and home offices.
- Optional redundant power supply for added reliability.
Predictable Performance
- Delivers consistent, reliable security services across all deployments.
Simplified Deployment
- Optional Zero Touch Provisioning (ZTP) for easy and efficient scaling.
Centralised Administration
- Integrated with Panorama® network security management for streamlined control.
Maximised Security Investment
- Prevents business disruptions and enhances ROI with Strata™ Cloud Manager.
This comprehensive feature set makes Palo Alto Networks’ ML-Powered NGFW an ideal choice for businesses seeking innovative and robust cybersecurity solutions.
Why Do You Need Comprehensive Application Identification and Control?
The features in Palo Alto Networks' Next-Generation Firewalls are essential for modern organisations because they address key challenges in securing and managing network traffic in an increasingly complex digital environment:
1. Protecting Against Sophisticated Threats
- Challenge: Cybercriminals use evasive techniques and encryption (like SSL/TLS) to hide malicious activities in network traffic, bypassing traditional security tools.
- Solution: By inspecting all application traffic, regardless of the port, protocol, or encryption, Palo Alto Networks ensures that threats are identified and stopped before they can cause harm.
2. Managing the SaaS Explosion
- Challenge: The rise of Software-as-a-Service (SaaS) applications has introduced a flood of sanctioned (approved) and unsanctioned (shadow IT) apps into corporate networks, increasing the risk of data loss and breaches.
- Solution: Automatic discovery and control of SaaS applications help organizations maintain visibility and enforce security policies, ensuring sensitive data isn’t exposed through unsafe or unauthorised apps.
3. Enabling Secure and Flexible Policies
- Challenge: Traditional port-based security rules are ineffective against modern, application-centric threats and are difficult to manage.
- Solution: Using the application itself—not just the port—as the basis for policy decisions ensures precise control. Organisations can allow or block specific applications, apply traffic-shaping, or inspect data based on real needs, improving both security and network performance.
4. Preventing Data Loss and Malware Infections
- Challenge: Cyberattacks often involve the exfiltration of sensitive data or the delivery of malicious files within application traffic.
- Solution: By analysing payload data within applications, the system can block malicious files, detect unauthorised data transfers, and prevent breaches.
5. Simplifying Network Management
- Challenge: Legacy Layer 4 rule sets are cumbersome and prone to errors, making networks harder to secure and maintain.
- Solution: The Policy Optimiser helps organizations migrate to modern, App-ID-based rules that are more secure, efficient, and easier to manage.
6. Gaining Visibility into Network Activity
- Challenge: Without insight into application traffic, organizations struggle to make informed decisions about security and resource allocation.
- Solution: Detailed reports on application usage—including SaaS traffic—help IT teams understand network activity, identify risks, and optimise their security policies.
Comprehensive application identification and control are no longer optional; they’re critical for:
- Protecting against modern cyber threats.
- Ensuring regulatory compliance.
- Preventing data breaches.
- Streamlining operations in an increasingly application-driven world.
Organisations need these capabilities to stay secure, efficient, and competitive in today’s digital age.
Why Organisations Need Security Enforcement for Users Anywhere, on Any Device
Modern organisations face increasing challenges in ensuring robust security for their users, especially as workforces become more distributed and mobile. Here’s why enforcing security for users at any location, on any device, is critical:
1. Protecting a Distributed Workforce
- Challenge: Remote and hybrid work environments mean employees access sensitive data from various locations, devices, and networks, creating potential security gaps.
- Solution: Enforcing consistent security policies ensures that users are protected, whether they’re in the office, at home, or on the go, reducing the risk of unauthorised access or data breaches.
2. Addressing Device Diversity
- Challenge: Employees use a wide range of devices, from desktops and laptops to smartphones and tablets, with different operating systems and configurations.
- Solution: Policies that adapt seamlessly to devices—whether iOS, Android, Windows, macOS, Linux, or virtual desktop interfaces (VDIs)—ensure comprehensive protection regardless of the endpoint.
3. Dynamic and Context-Aware Policies
- Challenge: Security needs change depending on user activities and behaviors, but traditional static policies can’t adapt in real-time.
- Solution: Dynamic User Groups (DUGs) allow time-bound or activity-specific policies, enabling quick, targeted responses to potential threats without waiting for directory updates.
4. Visibility Beyond IP Addresses
- Challenge: Traditional security models based on IP addresses fail to account for user behaviour or identity, limiting the ability to enforce user-specific policies.
- Solution: User and group-based visibility and policy enforcement provide granular control, allowing organisations to tailor security to individual needs while maintaining audit trails for reporting and forensics.
Use Cases
1. Securing Remote Work
- Scenario: An employee accesses sensitive company data from a café using their personal laptop.
- How It Helps: The firewall enforces security policies based on the user’s identity, ensuring data encryption and blocking access to unauthorised apps, regardless of location or device.
2. Dynamic Threat Mitigation
- Scenario: A user’s credentials are flagged as compromised, requiring immediate action.
- How It Helps: Using DUGs, administrators can automatically isolate the user, restrict access, and apply additional security measures until the issue is resolved.
3. Protecting Bring Your Own Device (BYOD)
- Scenario: Employees use personal devices for work but connect to the corporate network without proper oversight.
- How It Helps: Consistent policies ensure that all devices comply with security requirements, preventing unauthorised data transfers or malware infections.
4. Streamlined Compliance
- Scenario: A healthcare organisation needs to enforce HIPAA-compliant policies across devices used by medical staff.
- How It Helps: Policies are applied uniformly across devices, ensuring compliance with industry regulations without manual configuration.
5. Centralised Policy Management for Global Teams
- Scenario: A global company has teams operating across multiple countries with varying security risks.
- How It Helps: The solution ensures that all users, regardless of their geographic location, follow consistent security policies tailored to their roles and activities.
Organisations need robust, flexible security enforcement to:
- Protect remote and mobile workforces.
- Ensure consistent policy application across diverse devices and environments.
- Adapt policies dynamically based on user activity.
- Provide visibility and control that extends beyond traditional IP-based systems.
By addressing these needs, organisations can enhance their security posture, reduce vulnerabilities, and support secure, efficient operations in today’s highly connected world.
Why Organisations Need SD-WAN Functionality and Integrated 5G Cellular Modems
In the modern, distributed network landscape, organisations require reliable, secure, and flexible solutions to support their connectivity needs while maintaining optimal performance and security. Here's why SD-WAN functionality and integrated 5G cellular modems are essential:
1. Simplifying SD-WAN Adoption
- Challenge: Complex and expensive deployments for SD-WAN functionality.
- Solution: Palo Alto Networks enables SD-WAN directly on existing firewalls, eliminating the need for additional appliances or separate infrastructure. This simplifies implementation and reduces costs.
2. Enhancing Security for SD-WAN
- Challenge: Traditional SD-WAN solutions often lack robust, integrated security, leaving networks vulnerable to cyber threats.
- Solution: Palo Alto Networks’ SD-WAN is natively integrated with its industry-leading security capabilities, ensuring that all traffic is protected without the need for standalone security appliances.
3. Delivering Superior End-User Experience
- Challenge: Network issues like latency, jitter, and packet loss impact critical applications, leading to poor user experiences.
- Solution: By optimising traffic routing and leveraging advanced quality-of-service (QoS) controls, Palo Alto Networks’ SD-WAN minimizes latency, jitter, and packet loss, delivering an exceptional experience for users and applications.
4. Ensuring Network Uptime with Integrated 5G
- Challenge: Organisations often face network outages or degraded WAN performance that disrupt business-critical applications.
- Solution: The PA-415-5G appliance with an integrated 5G cellular modem offers:
- Backup WAN Transport: Provides high-speed 5G as a failover solution, ensuring network continuity during primary WAN outages.
- Primary WAN Connectivity for Mobile Businesses: Enables rapid deployment for businesses that rely on cellular connectivity as their primary WAN, reducing setup complexities.
5. Supporting Business Mobility
- Challenge: Mobile businesses, such as logistics fleets or pop-up retail operations, require flexible and rapid deployment of reliable WAN connectivity.
- Solution: The integrated 5G Next-Generation Firewall simplifies deployment by combining firewall security and cellular connectivity in one appliance, eliminating the need for additional hardware.
Use Cases
1. Ensuring Business Continuity
- Scenario: A retail chain experiences periodic outages on its primary WAN during high-traffic periods.
- How It Helps: The integrated 5G modem serves as a backup, ensuring critical applications like point-of-sale systems remain operational without interruption.
2. Supporting Remote Offices
- Scenario: A small branch office requires secure, high-performance WAN connectivity but lacks IT resources for complex installations.
- How It Helps: SD-WAN functionality, enabled on existing firewalls, provides a cost-effective, easy-to-deploy solution tailored to their needs.
3. Mobile Operations
- Scenario: A logistics company needs secure, always-on connectivity for its fleet.
- How It Helps: The PA-415-5G appliance provides cellular WAN connectivity combined with firewall security, ensuring rapid deployment and ongoing protection.
4. Optimising Application Performance
- Scenario: A software company needs consistent performance for video conferencing and cloud applications across multiple offices.
- How It Helps: SD-WAN minimises latency and packet loss, ensuring uninterrupted and high-quality application performance.
Why These Features Are Essential
- Seamless Connectivity: Combining SD-WAN with integrated 5G provides a flexible, reliable solution for organisations of all sizes and sectors.
- Cost Efficiency: Avoids the expense of separate SD-WAN and cellular appliances while simplifying network architecture.
- Future-Ready: Supports evolving business needs, including the growing reliance on remote work, mobile operations, and 5G technology.
- Improved User Experience: Ensures critical applications perform optimally, enhancing productivity and customer satisfaction.
Organisations adopting Palo Alto Networks’ SD-WAN and integrated 5G solutions gain a secure, high-performance network that adapts to their needs while ensuring uptime and application performance. These capabilities empower businesses to stay agile and competitive in today’s fast-paced digital environment.




Latest Insights

Ask us anything
No matter what your question relates to, our IT specialists will be happy to help with any related enquiries.
We want to hear from you
Send us your details and we’ll get back to you to schedule a time to talk.
Contact us form Konverge footer
We will get back to you as soon as possible
Please try again later







