How Security Approaches Must Evolve to Address Modern Network Threats
The Modern Network Threat: Why Legacy Approaches Fall Short

In today's digital age, the integration of IoT, cloud technologies, and remote work has dramatically expanded the attack surface for enterprises. The modern landscape demands a new approach to security that goes beyond the limitations of legacy tools. Traditional signature-based solutions struggle to keep up with sophisticated attackers and dynamic network environments. As cyber threats evolve, so must our security strategies.
Traditional security measures—once sufficient for static and centralised systems—are no longer effective. Instead, organisations must adopt solutions that leverage machine learning, centralised management, and flexible deployment to stay ahead of sophisticated attackers.
This page will summarise the ESG Whitepaper: How Security Approaches Must Evolve to Address Modern Network Threats. It explores the challenges of legacy systems, the emerging trends in cybersecurity, and how modern solutions provide the agility, scalability, and effectiveness needed in today’s threat landscape.
The Digital Transformation Impact on Security
Expanding the Attack Surface
Digital transformation is a double-edged sword. While it enables innovation and operational efficiency, it also introduces vulnerabilities. Key drivers of this expanded attack surface include:
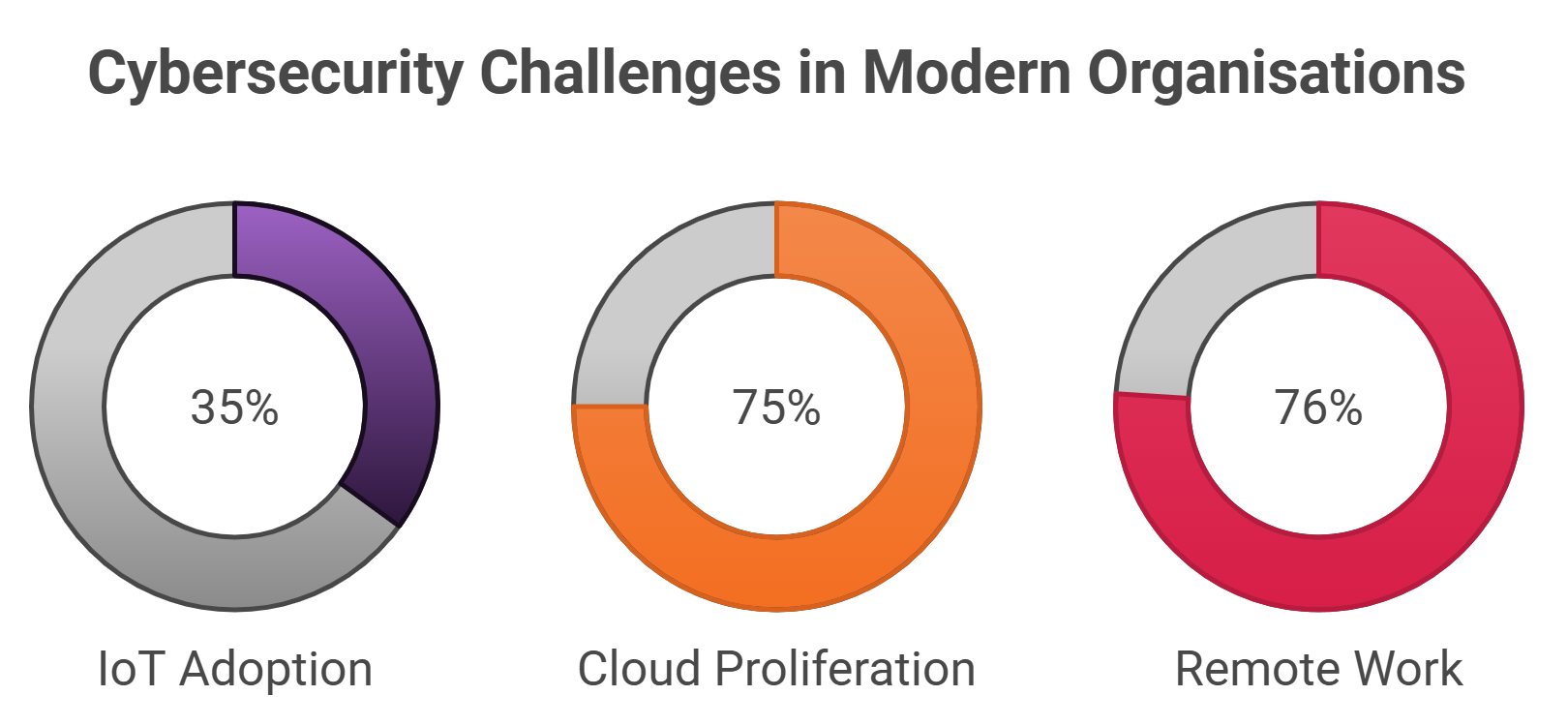
- IoT Adoption: 35% of organisations have ongoing IoT initiatives, with another 29% planning to launch soon. IoT devices, often deployed without robust security, serve as entry points for attackers.
- Cloud Proliferation: Three-quarters of organisations store sensitive data across multiple cloud platforms, increasing the risk of data breaches.
- Remote Work: The COVID-19 pandemic accelerated remote work adoption, with 76% of employees working from home at the peak of the crisis.
Legacy Tools: A Growing Liability
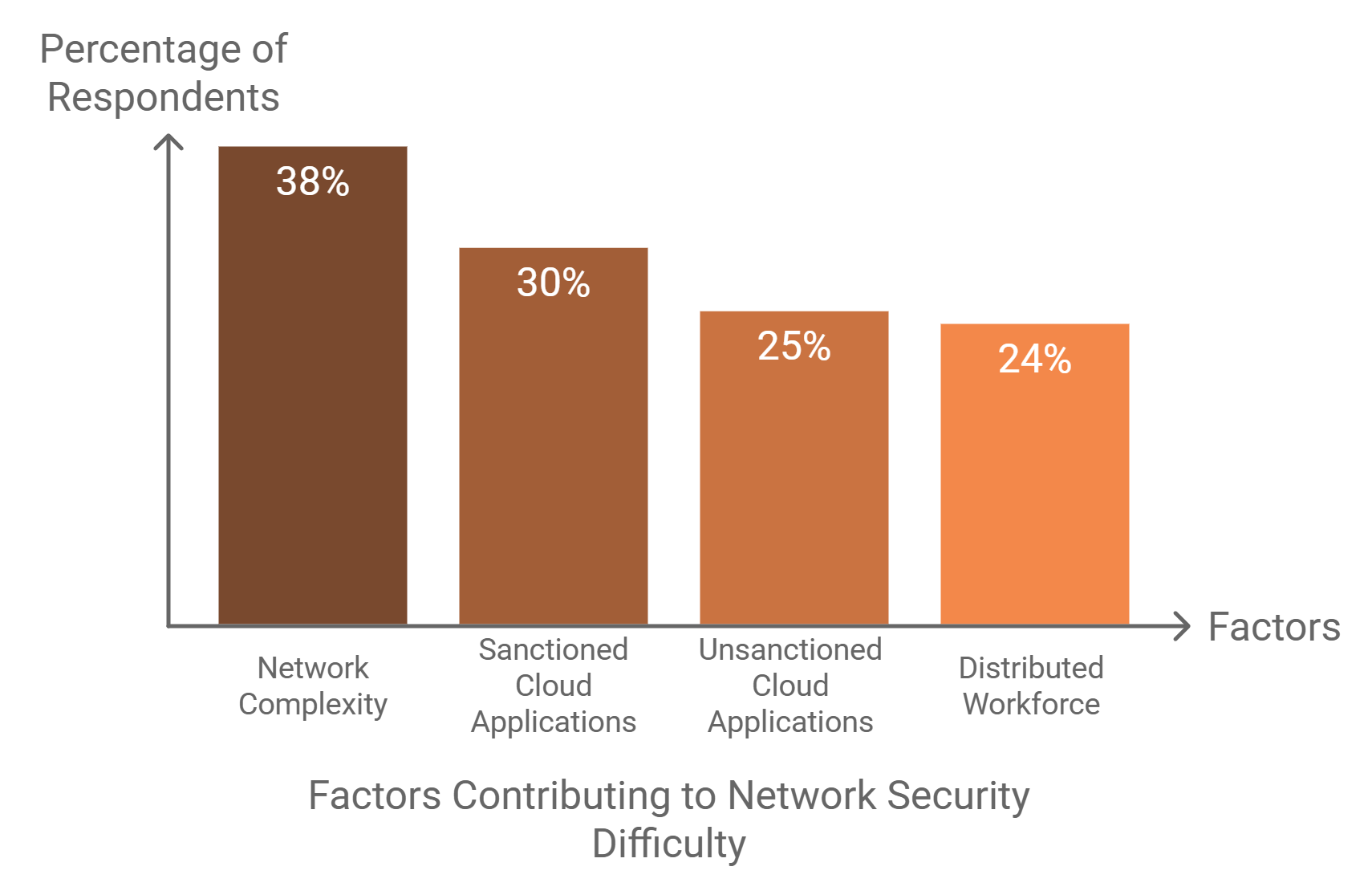
Legacy security solutions, characterised by signature-based and siloed approaches, struggle in this environment. According to recent surveys, 85% of organisations find network security more challenging than two years ago. The reasons are clear:
- Increased device diversity and network complexity.
- The rise of unsanctioned applications and distributed workforces.
- Sophisticated threats bypassing reactive defenses.
Why Legacy Security Approaches Fail
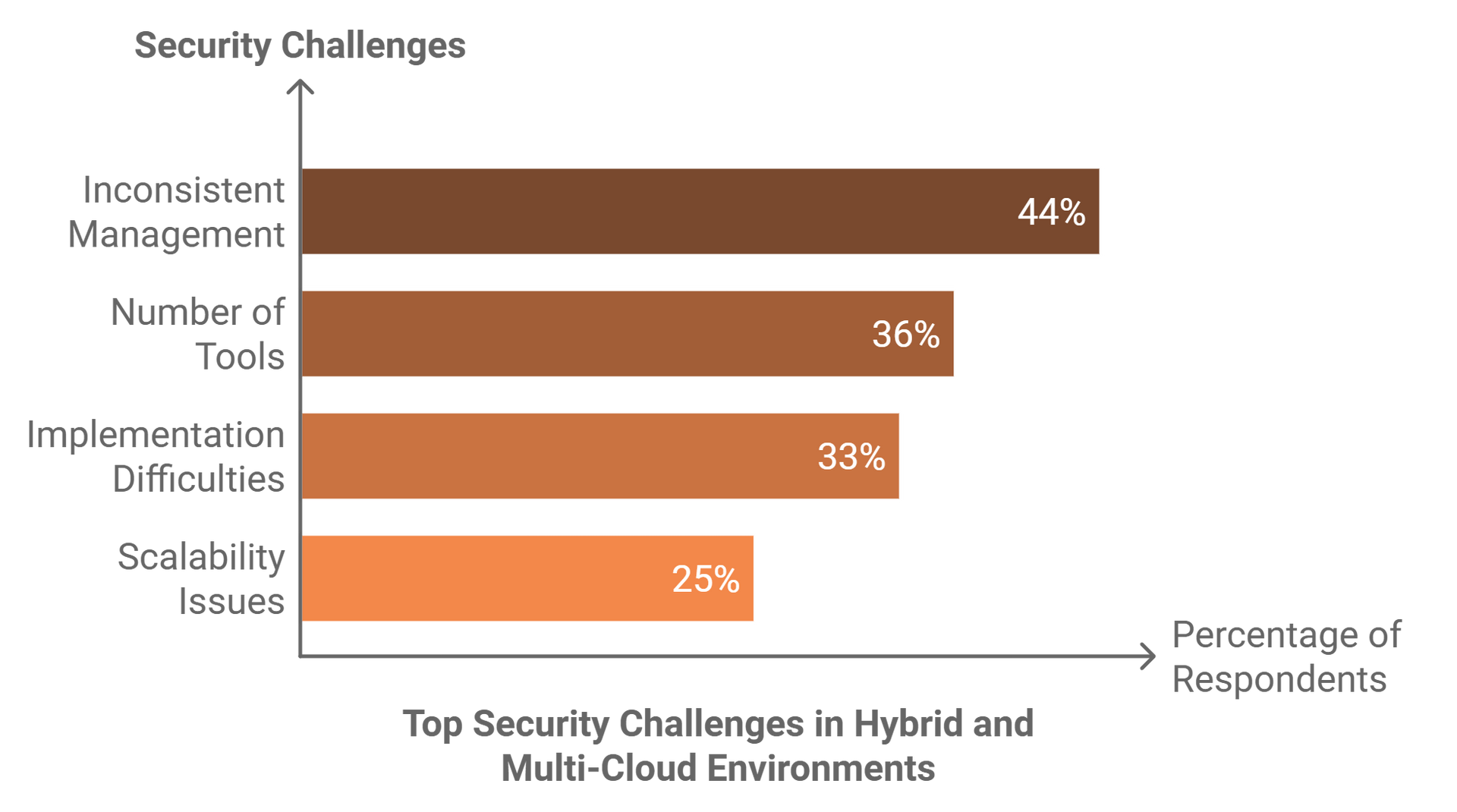
Inefficiency and Fragmentation
Legacy systems rely on multiple, independently managed tools. This fragmentation leads to:
- Human Error: Manual configurations increase the likelihood of mistakes.
- Inconsistent Policies: Enforcement varies across on-premises, cloud, and remote environments.
- Operational Bottlenecks: Teams struggle to scale security policies in dynamic networks.
The Performance Penalty
Backhauling traffic for inspection—common in traditional setups—introduces latency and degrades user experience. With users increasingly accessing cloud services directly, this approach is neither practical nor scalable.
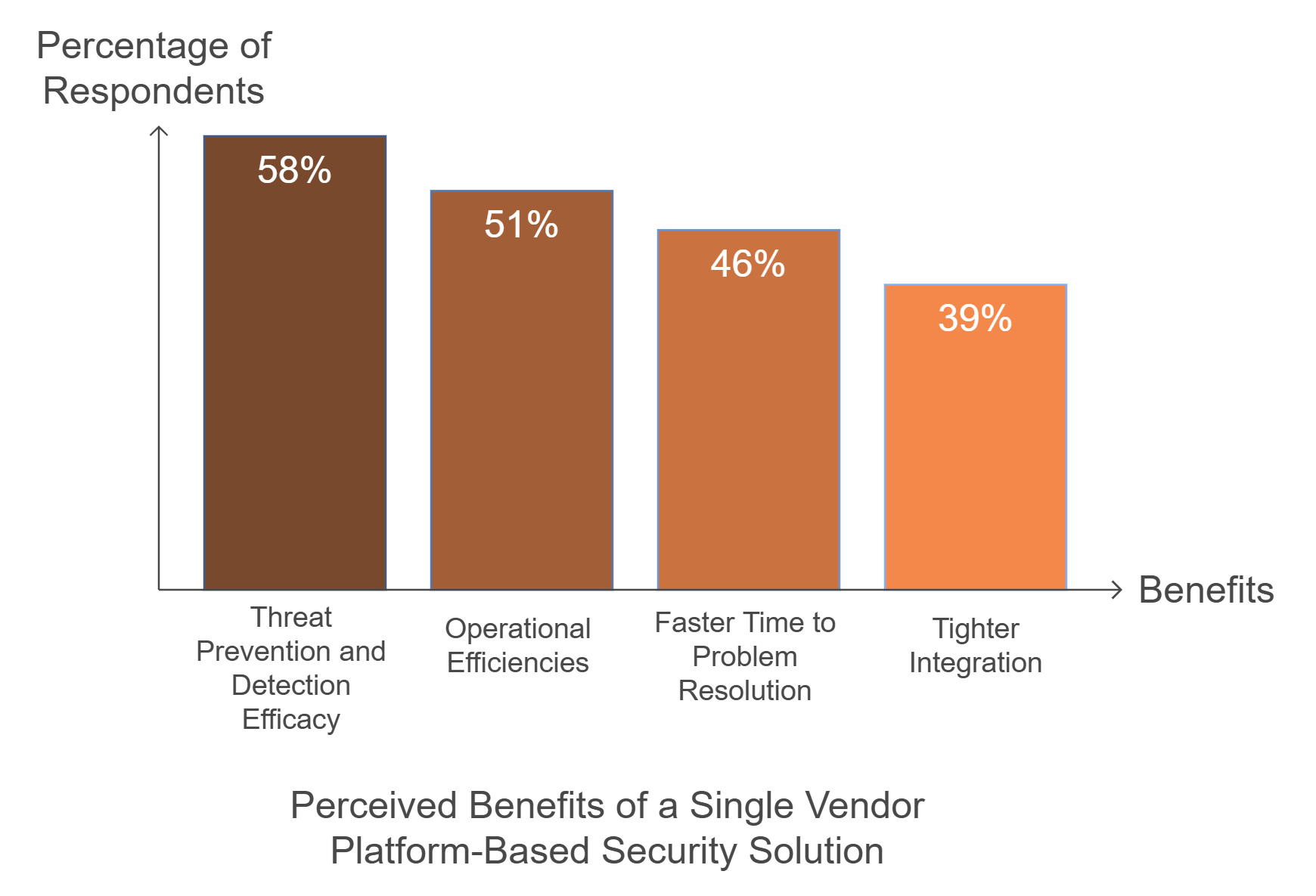
Attributes of Modern Security Platforms
To address today’s challenges, organisations need security platforms with the following features:
- Machine Learning Integration: Enables real-time threat detection and response.
- Consolidation: Reduces tool sprawl by combining best-of-breed capabilities into a unified platform.
- Centralised Management: Provides visibility and policy enforcement across diverse environments.
Machine Learning in Action
Machine learning transforms cybersecurity by analysing vast data sets to identify patterns and anomalies. This proactive approach improves threat detection rates and reduces reliance on signatures.
The Role of Flexibility in Security
Modern security solutions must accommodate varied environments, including:
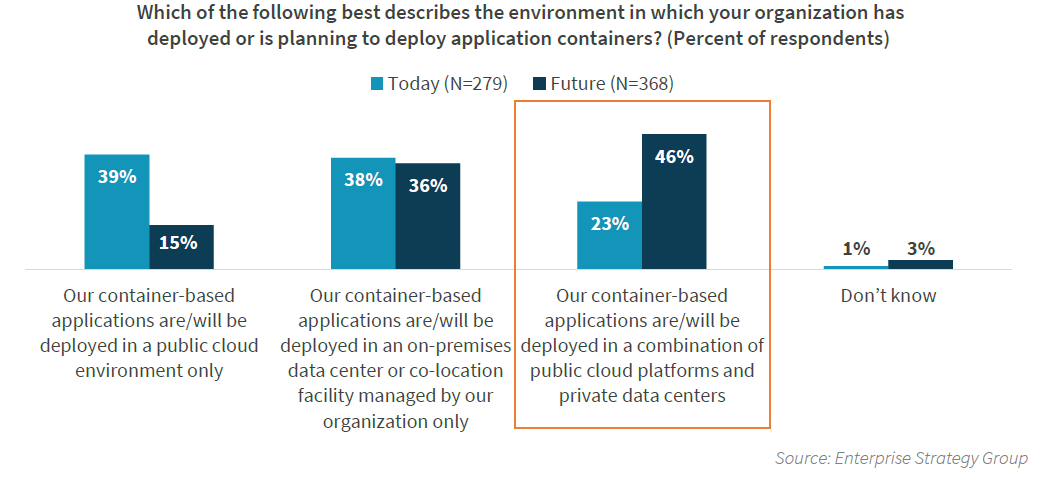
- Hybrid Multi-Cloud: With 46% of organisations deploying container-based applications across public and private clouds, flexibility is essential.
- IoT Security: IoT segmentation, anomaly detection, and device categorisation are critical for managing the influx of devices.
- SD-WAN Integration: Secure SD-WAN solutions streamline traffic routing without compromising security.
Hybrid Cloud Adoption Will Increase with the Use of Containers
The Future of Network Security
Centralised Management and Automation
The complexity of modern networks necessitates centralised management tools that:
- Automate policy generation based on machine learning insights.
- Provide consistent enforcement across environments.
- Support granular, role-based administration.
Subscription-Based Flexibility
Subscription models allow organisations to scale security capabilities as needed. Advanced features like malware detection, DNS protection, and data loss prevention can be added seamlessly.
Embracing a Proactive Security Model
The evolving threat landscape requires organisations to rethink their security strategies. By adopting platform-based solutions with integrated machine learning, centralised management, and flexible deployment, enterprises can enhance their resilience against sophisticated attacks.
As attackers grow more innovative, the need for proactive, adaptive, and scalable security solutions has never been greater. Modern security platforms not only protect organisations but also empower them to innovate without fear.