Reducing complexity is no longer just a good idea – it’s the only way to keep businesses productive, cut costs and prevent risk from spiraling out of control.
Third Party Cyber Risks and Management
Third-Party Risk: A Comprehensive Guide
Topics
The concept of third-party risk has become more critical than ever as businesses become more interconnected and rely on a web of external parties to streamline operations. From vendors and suppliers to service providers and contractors, external entities often have access to sensitive data, posing potential threats to an organisation's security posture.
The Australian Government Office of the Australian Information Commissioner reported 70% of data breaches from January 2023 to June 2023 was due to malicious or criminal attack, 26% was due to human error, and 4% was a result of a system fault. And 42% of all data breaches resulted in cyber security incidents as shown in the below graph.

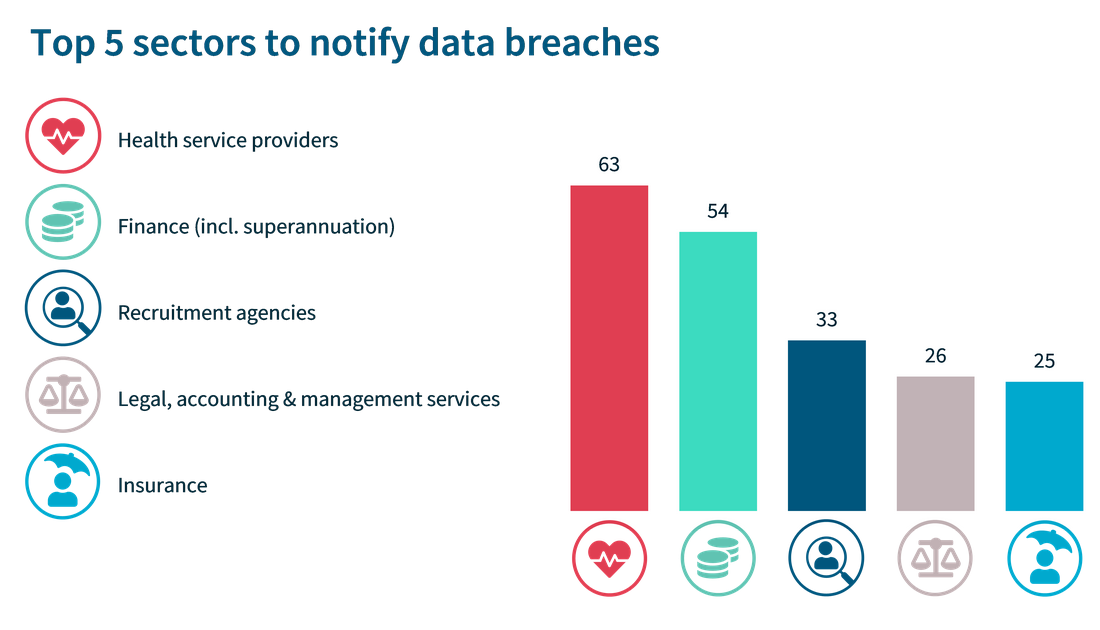
Top Sectors to Notify Data Breaches
The Notifiable Data Breaches (NDB) scheme seeks to safeguard individuals by mandating the notification of potential harm from a data breach. Prompt notification enables individuals to proactively take measures to safeguard themselves, including heightened awareness of potential scams. Any delays in identifying, evaluating, and communicating breaches may increase the likelihood of individuals experiencing harm.
The OIAC reports the top 5 sectors that have notified them of data breaches.
Under Australian Privacy Principle (APP) 11, organisations must take reasonable steps to protect the data they hold from misuse, interference and loss, and from unauthorised access, modification or disclosure. As part of complying with APP 11, organisations should ensure they have measures to prevent and promptly detect data breaches.
The Australian Signals Directorate (ASD) is a government intelligence agency with a dual focus on foreign signals intelligence and cybersecurity. The agency works closely with intelligence agencies and international partners, sharing information and resources to strengthen Australia's national security. The diverse and driven team at ASD operates in the challenging space between the difficult and the impossible, pushing technology limits to ensure the safety and prosperity of Australians. ASD collects and analyses electronic signals to inform and protect Australia's interests, including addressing issues like terrorism, weapons proliferation, organised crime, and cyber threats. In the realm of informing, ASD's intelligence analysts produce reports, offering insights and recommendations, collaborating with other agencies.
Top Routinely Exploited Vulnerabilities
ASD published a report of top routinely exploited vulnerabilities coauthored by cybersecurity agencies forming joint Cybersecurity Advisory (CSA) including:
- United States: The Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and Federal Bureau of Investigation (FBI)
- Australia: The Australian Cyber Security Centre (ACSC)
- Canada: Canadian Centre for Cyber Security (CCCS)
- New Zealand: New Zealand National Cyber Security Centre (NCSC-NZ) and Computer Emergency Response Team New Zealand (CERT NZ)
- United Kingdom: National Cyber Security Centre (NCSC-UK)
The advisory detailed Common Vulnerabilities and Exposures (CVEs) frequently exploited by malicious cyber actors in 2022, emphasising that older software vulnerabilities were targeted more than recently disclosed ones. The agencies stressed the importance of implementing recommendations to reduce the risk of compromise by malicious cyber actors, urging action from vendors, designers, developers, and end-user organisations.
Types of Third-Party Data Risks
Common third-party risks can be categorised into three main types based on their potential impact on businesses:
1. Financial/Reputational Risks:
Risks that pose a threat to your revenue or reputation due to actions of a third party. For example, your reputation is at risk if a supplier delivers a faulty component for your products, impacting customer trust and potentially harming revenue.
2. Legal and Regulatory Risks:
Risks that arise when a third party affects your compliance with legislation or regulations. For example, if a supplier violates labour or environmental laws, your organisation can still be held accountable, emphasising that outsourcing does not absolve responsibility for legal compliance.
3. Operational Risks
Risks that stem from a third party's potential to disrupt your day-to-day operations. For example, a software vendor getting hacked, resulting in a system outage and disrupting your business operations.
It's important to note that these categories may overlap, for example, a data breach. While primarily a regulatory threat, can also have operational implications by disrupting systems and processes. Recognising and mitigating these various third-party risks is crucial for maintaining the overall security and resilience of a business.
Cybersecurity Advisory (CSA) Mitigation Recommendations to Reduce Security Risk
CSA recommend end-user organisations implement the mitigation measures listed below to improve cybersecurity posture on the basis of the threat actors’ activity. The mitigation measures listed also align with the cross-sector Cybersecurity Performance Goals (CPGs) developed by CISA and the National Institute of Standards and Technology (NIST). These are the baseline set of practices and protections that CISA and NIST recommend all organisations implement in four key areas: Vulnerability and Configuration Management, Identity and Access Management, Protective Controls and Architecture, and Supply Chain Security.
Vulnerability and Configuration Management
- Timely update software, operating systems, applications, and firmware.
- Prioritise patching known exploited vulnerabilities, especially those identified in the advisory.
- Implement vendor-approved workarounds if a patch cannot be quickly applied.
- Conduct routine automated asset discovery and maintain a robust patch management process.
- Document secure baseline configurations, perform regular backups, and update incident response plans.
Identity and Access Management
- Enforce phishing-resistant multi-factor authentication (MFA) for all users.
- Apply MFA to all VPN connections and regularly review privileged accounts.
- Configure access control under the principle of least privilege.
- Ensure software service accounts only provide necessary permissions.
Protective Controls and Architecture
- Properly configure and secure internet-facing network devices.
- Implement Zero Trust Network Architecture (ZTNA) to limit lateral movement.
- Continuously monitor the attack surface using security tools.
- Use web application firewalls and administrative policies to enhance security.
- Employ a network protocol analyser to examine captured data.
Supply Chain Security
- Reduce third-party applications and unique system/application builds.
- Ensure contracts with vendors require notification of security incidents and vulnerabilities.
- Request Software Bill of Materials (SBOM) from vendors to enhance vulnerability monitoring.
- Inquire about software providers' secure by design programs and their efforts to remove vulnerabilities.
Forcepoint enabling safe use of data and consistency of results
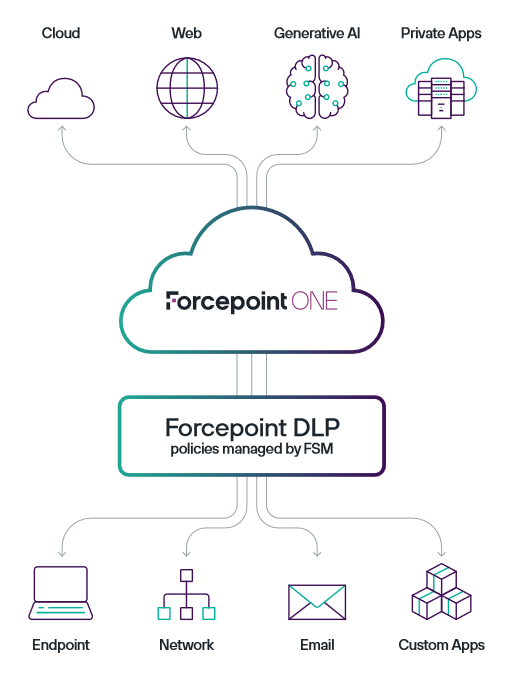
Organisations have traditionally used different tools to manage data security, privacy, governance, and compliance. We noticed Forcepoint as a strong contender in the SASE offering due to its flexible and seamless one SASE vendor solution. It adds all-in-one Zero Trust with industry-leading Data Loss Prevention (DLP) and advanced threat protection throughout their Cloud Access Security Broker (CASB), Secure Web Gateway (SWG) and Zero Trust Network Access (ZTNA) services. It enables a security of your data wherever and however it is accessed.
Six ways that Forcepoint ONE SASE is different
Forcepoint ONE brings together six (6) key elements to deliver the security and networking that organisations need to be successful in today’s technological environment:
1. Data-first: Enterprise-class data security everywhere
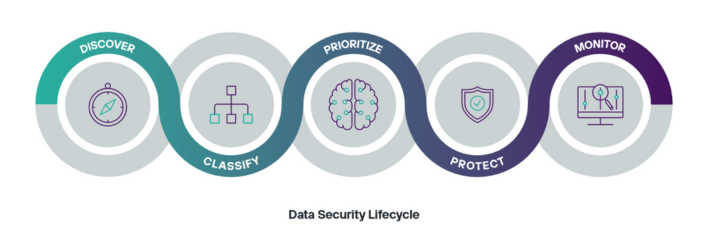
Forcepoint emphasises a unique perspective on cybersecurity, focusing on enabling the secure use of sensitive data anywhere. They integrate robust data security technology into their Forcepoint ONE platform and SSE gateways, covering CASB, SWG, and ZTNA. Their Data Loss Prevention (DLP) technology, recognised as a leader by industry analysts, is part of a Zero Trust-based framework called the Data Security Lifecycle. This lifecycle automates steps to efficiently protect data from unauthorised access, theft, or accidental loss. Forcepoint's approach involves classifying and organising data, allowing for the creation and enforcement of dynamic security policies beyond basic pattern matching. The Forcepoint ONE platform simplifies policy definition with a comprehensive library of templates, ensuring consistent application across various channels. Notably, administrators can apply granular data security controls to web-based apps using Field Programmable SASE Logic (FPSL), enabling customisation based on HTTP request attributes. Forcepoint ONE supports safe usage of cloud and internal web apps from diverse devices, including BYOD and agentless devices, to enhance productivity without compromising data security. For example, Forcepoint ONE can easily:
→ Block logins to corporate SaaS applications using a personal email address.
→ Log every file uploaded to personal Google Drive accounts for users in a risky-users group.
→ Block likes in Facebook.
→ Only let members of the marketing group post to LinkedIn.
→ Block sensitive content in a Twitter post.
And, since people in today’s workforce often depend upon phones, tablets and endpoints such as Linux workstations
or Chromebooks, Forcepoint ONE makes it possible to safely use cloud and internal private web apps from BYOD
and other agentless devices to keep people productive without putting data at risk.
2. Single-vendor: Security and SD-WAN in one
Forcepoint is a leader in integrating security and networking technologies into a unified product managed from a single console. Their Secure SD-WAN solutions were early in combining SD-WAN routing with high-security firewall and intrusion prevention technologies. The patented multi-link, multi-ISP aggregation globally transforms legacy wide area networks (WANs) into modern, broadband-based SD-WAN, supporting massive scalability. Forcepoint Secure SD-WAN allows the management of policies for up to 6,000 sites from a single console, connecting distributed organisations directly to the internet for optimal performance in accessing cloud applications. Advanced features like application steering, health monitoring, and zero-touch updating contribute to proactive IT management, ensuring consistent performance and uptime while minimizing infrastructure costs. This SD-WAN serves as a foundation for implementing a converged Secure Access Service Edge (SASE) architecture, allowing organizations to route traffic for various applications to Forcepoint ONE Security Service Edge (SSE) gateways in the cloud. This approach not only simplifies the protection of employees and business data but also enables the definition and enforcement of security policies for unmanaged devices, including guest laptops, BYOD devices, printers, and Internet of Things (IoT) devices.
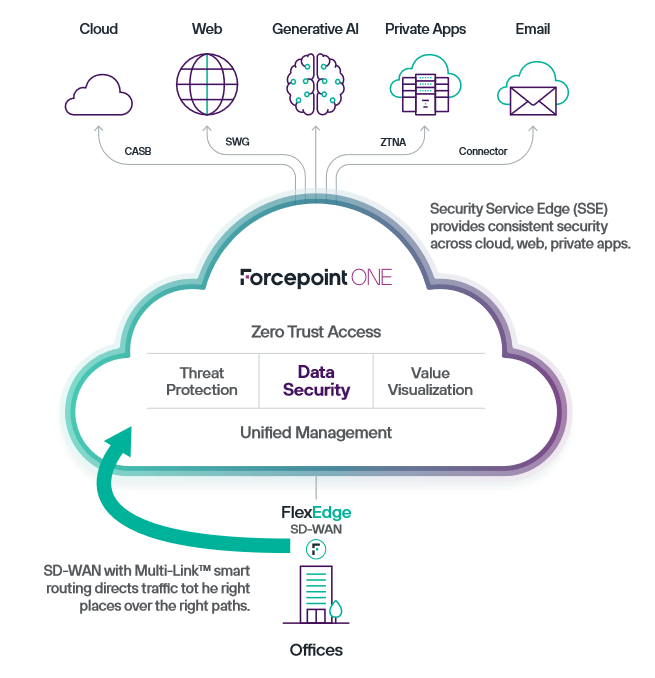
3. Simplified Architecture: converged, unified management
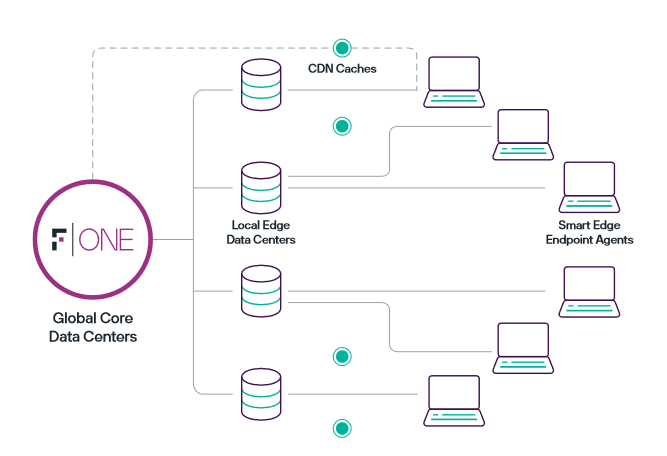
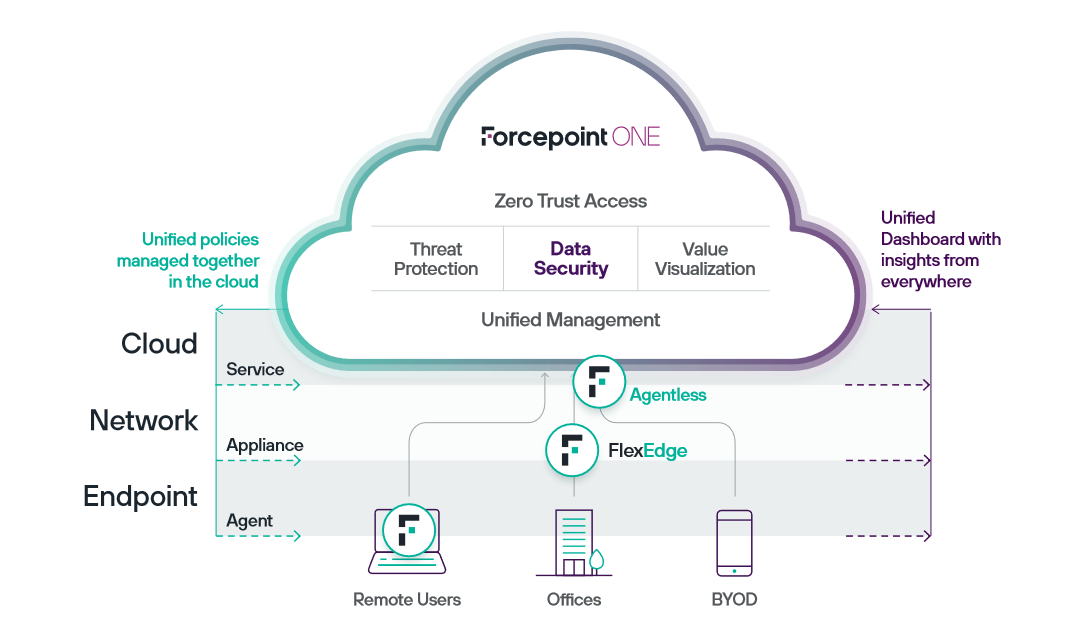
Forcepoint's mission is "Security Simplified," recognising the need to streamline security infrastructure as IT environments evolve and teams face increasing challenges. Forcepoint ONE, the core of their approach, is designed to eliminate gaps and redundancies in fragmented technologies. Key elements include Zero Trust-based access gateways, advanced threat protection services, leading-edge data security services, secure agentless access from BYOD and unmanaged devices, interactive dashboards for performance indicators, and a unified console for policy management. The platform adopts a multi-tier architecture with global core data centers handling primary functions, local edge data centers acting as CDN caches, and Smart Edge endpoint agents providing additional capabilities. The SmartEdge software integrates with other endpoint and network controls to offer a single endpoint application for comprehensive Forcepoint ONE connectivity and security. This approach aims to simplify security, enhance productivity, cut costs, and prevent risks from escalating.
4. Based on Zero Trust principles
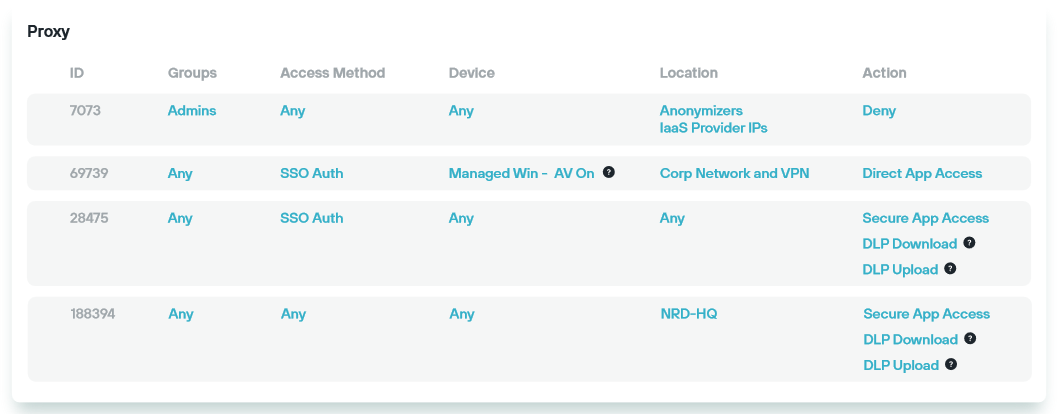
Forcepoint ONE access services are governed by a Zero Trust approach, focusing on specifying the identity, application, devices, and location for each action. This involves creating data security and threat prevention policies for all uploads and downloads, integrating user notification and coaching to enhance user and data protection.
In terms of economic value, Forcepoint ONE offers administrators comprehensive visibility and unified reporting across both managed and unmanaged devices. Insights dashboards provide a consolidated view of activities across various security services, shedding light on the business value delivered by Forcepoint. This approach aims to ensure a clear understanding of the security landscape and its impact on the organisation.
5. Multi-tier, Distributed Enforcement across cloud, network edge and endpoint
The cloud and internet have transformed security management, and Forcepoint ONE, as a unique SASE platform, goes beyond traditional solutions. It disperses enforcement of networking and security policies to the user endpoint, network infrastructure, and cloud applications. This distributed approach optimises application performance, reduces network bandwidth usage, and eliminates issues associated with redirecting traffic through chokepoints. Forcepoint ONE ensures consistent policy enforcement and monitoring through unified dashboards.
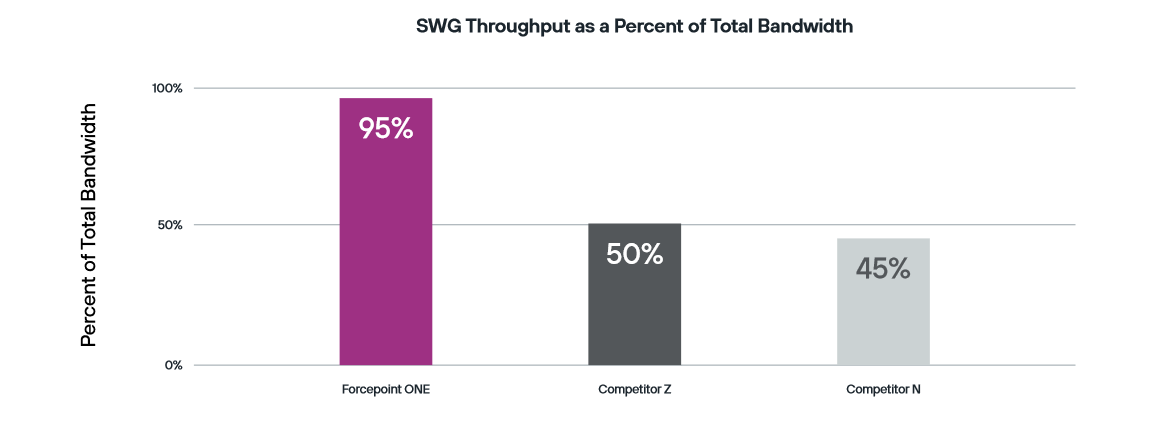
For example, it addresses challenges posed by traditional SWG architectures, such as latency, bandwidth utilisation, location awareness, and compliance issues. Forcepoint ONE's SmartEdge software acts as a cloud onramp, optimising application performance and user experience by routing traffic based on policies. SmartEdge helps in scenarios like new URL access, SWG risky website protection and isolation, and secure file movement to/from unsanctioned web applications. This distributed enforcement approach in Forcepoint ONE offers up to twice the browsing performance compared to cloud-only systems, providing robust protection against web-borne threats and unauthorized data uploading.
Microsoft advises Microsoft 365 users against using proxies, creating a dilemma for organisations that must choose between productivity and security. Forcepoint ONE resolves this by allowing the enforcement of web security policies, including those for data loss prevention, directly on endpoints using their SmartEdge software. SmartEdge acts as a "cloud onramp," automatically directing traffic to the relevant service or application based on the accessed content. This solution complements the cloud proxies provided by Forcepoint ONE, which are designed to secure agentless devices like BYOD (Bring Your Own Device) and IoT (Internet of Things). Overall, Forcepoint ONE provides a comprehensive approach to security, ensuring both productivity and protection.
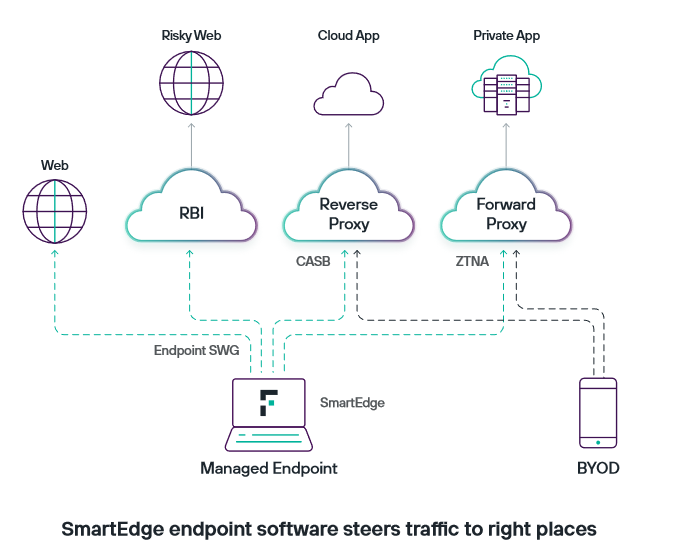
SmartEdge is especially beneficial for remote users, offering a natural, productive, and secure user experience. This technology collaborates with the Forcepoint ONE cloud platform to ensure the consistent enforcement of policies in various scenarios. The distributed enforcement strategy within Forcepoint ONE not only provides up to twice the browsing performance compared to cloud-only systems but also ensures comprehensive protection against web-borne threats and unauthorised uploading of sensitive data. This integrated approach aims to optimise user experience while maintaining robust security measures.
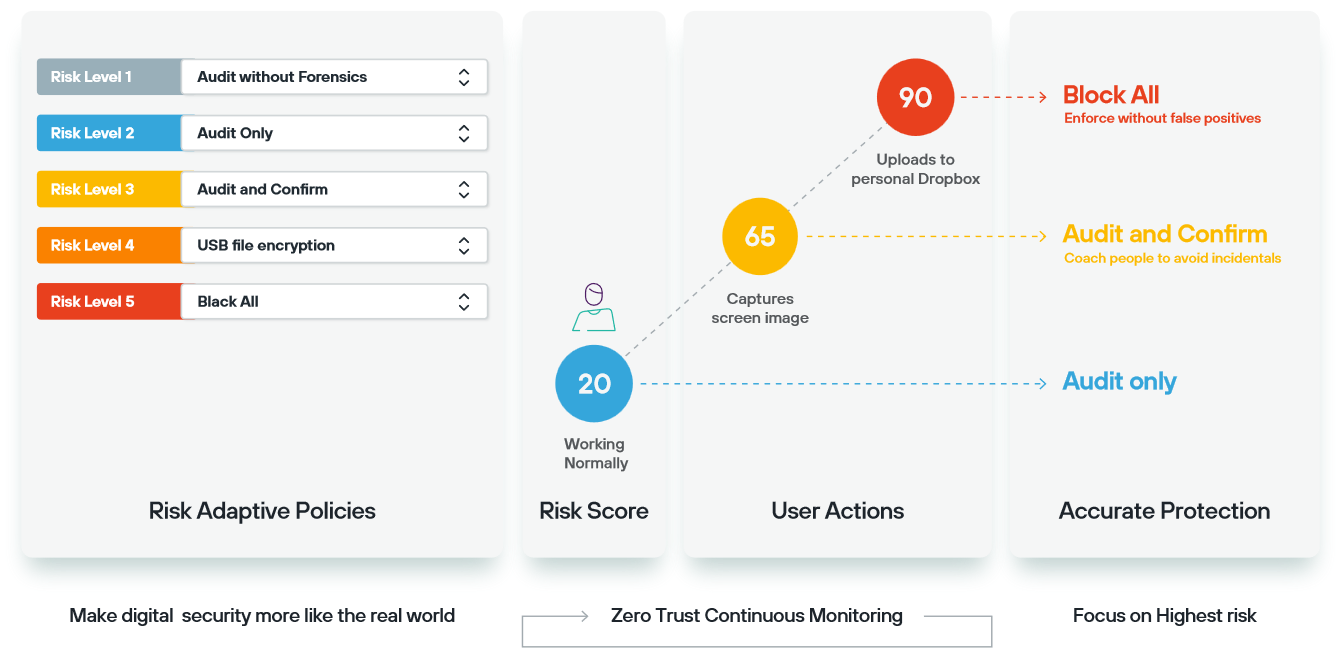
6. Risk-adaptive protection for contextual security
In the current dynamic work environment where people operate from various locations and data is scattered everywhere, creating individual policies for different combinations of users, devices, locations, and applications becomes error-prone and impractical. Forcepoint recognises the limitations of such a static approach, especially in real-world scenarios where individuals with good judgment need flexibility in using sensitive data, with stricter controls in place when mistakes occur.
Forcepoint pioneers a "risk-adaptive" protection strategy, dynamically selecting and enforcing policies based on users' actions, device compliance with corporate guidelines, the sensitivity of the data involved, and other relevant factors. This approach automates and personalizes security measures, granting users the freedom to utilize sensitive data innovatively while concentrating enforcement on critical situations. Forcepoint integrates this technology into its enterprise Data Loss Prevention (DLP) solutions, safeguarding data across various channels, including endpoint devices, networks, email, and cloud and web applications secured with Forcepoint ONE's Security Service Edge (SSE) services. The outcome is enhanced user productivity, reduced operating costs (simplified policy definition, fewer urgent helpdesk calls regarding user blocks), and diminished security risks.
Delivering data security everywhere – even for generative AIs
Emerging innovations like ChatGPT and others, which represent a new form of "shadow IT" with potential risks to sensitive data, Forcepoint addresses the challenge by allowing organisations to harness the productivity gains of generative AIs while maintaining control. This control includes limiting access to authorised groups or individuals, managing file uploads and cut-and-paste actions, and inspecting and protecting sensitive data to prevent leakage. Forcepoint's approach balances the advantages of generative AIs with robust security measures.
Book a discovery call with Konverge and Forcepoint
We are pleased to advise that Konverge is a Forcepoint partner and we're here to journey to increase productivity, cut-costs, reduce data risks and streamline compliance.
Simply complete the below form and one of our technical specialists will be in touch.
Contact Us - Forcepoint Discovery
We will get back to you as soon as possible.
Please try again later.



Latest Insights

Ask us anything
No matter what your question relates to, our IT specialists will be happy to help with any related enquiries.
We want to hear from you
Send us your details and we’ll get back to you to schedule a time to talk.
Contact us form Konverge footer
We will get back to you as soon as possible
Please try again later